Five Ways to Get into Fifth Gear in the Office
At Rocket IT, we’ve adopted the Five Gears practice created by our friends at GiANT Worldwide to help us communicate better with each other in the office. If you’re not familiar with the tool, the five gears represent different modes any one of us is in at any point throughout the day. Each gear represents…
Read MoreSeven Password Mistakes and How to Avoid Them
A different security breach hits the headlines on an almost daily basis. While you may not be too concerned about the safety of your LinkedIn profile after a quick password reset, you may still be committing some of the most common password mistakes. We’re sure your password is more secure than “password” (especially after our…
Read MoreThe Importance of Documentation For Your Network
You have a newsletter that goes out to all your clients and community fans every month. You have sales prospects that you keep tabs on and check-in with. You have a history of your interactions with your clients within your client relationship management (CRM) software. But do you actually have these processes documented? There’s a…
Read MoreUsing Outlook Calendar For Effective Large Group Scheduling
Outlook’s scheduling functions are entirely underutilized. The problem? Many people aren’t aware of the advanced capabilities Outlook Calendar has or how much easier it is to use shared calendar scheduling. Outlook is here to help do the heavy lifting for you. Large Group Outlook Scheduling Foundation To lay a foundation, the first place to start…
Read MoreI Was Sold the Right Service at the Right Time
Salespeople. I am one, so I’m keenly aware of the truth in this statement: “No one likes to be sold, but everyone likes to buy.” Recently, I went to an oil change place near my office. Why did I go? Because I needed my oil changed. Also, they had good online reviews and were convenient.…
Read MoreWhat Mac Users Should Know About the New Ransomware
Mac users beware, you’re no longer safe from ransomware. The ransomware dubbed KeRanger recently hit Macs, infecting about 6,000 computers before it was caught and shut down. While this isn’t the first virus aimed at Macs, this is the first one that has gotten through Apple’s defenses. The KeRanger ransomware is a Mac version of…
Read MoreKeeping Out Locky Ransomware
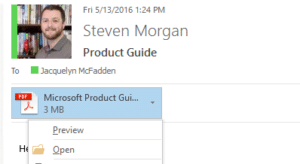
“Locky” is the newest villain on the Ransomware scene. Since Hollywood Hospital fell prey to the hackers, the tech world has been on high alert. So how does such a high-profile organization become a victim to ransomware like Locky? The virus disguises itself in a Word document attached to an email. The Word document itself…
Read MoreFrom Intern to Full-Time: Why Your Employee Onboarding Process is Crucial to Success
How to stand out to potential new employees has been a topic before on the Rocket IT blog – through benefits from working remotely to building programs that help them thrive. But there is another way outside of the working hours of 9-5 to help your employees and attract the rockstars you’re looking for. Investing…
Read More