Parler Returns to App Store | Previous Breach Leading to Parler’s Demise

Social Media platform, Parler found itself in hot water after its services were used to assist in the planning of the attack on the United States Capitol on January 6, 2021. However, after just three months, the app is set to make a comeback to the Apple App Store.
What is Parler?
With its initial launch in 2018, Parler promised individuals an alternative platform to that of mainstream social media. While popular sites, such as Twitter, Facebook, and Instagram, enact moderation and policies to prevent the spread of misinformation and violence, Parler’s promise of “free speech” was not without its consequences. With little to no administrative interference in place, the service immediately proved to be a breeding ground for extremist groups, fraudulent news organizations, and conspiracy theorists.
As a result of these actions and the unwillingness to intervene, Parler naturally morphed into a key resource for those groups that planned the attack that left five individuals fatally wounded at the U.S Capitol.
How Was Parler Breached?
Noting Parler’s role in eliciting these riots, it became clear that the up-and-coming social media platform was on a quick and steady decline. But before the service could fade completely, one researcher with the Twitter handle @donk_enby, found it her responsibility to pull information from Parler’s code that could be useful for future researchers, law enforcement, and historians.
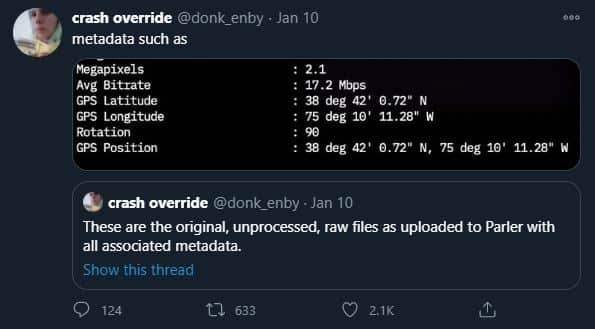
In a matter of days, @donk_enby used data scraping techniques to analyze 1.1 million URLs of videos that were uploaded to the service over the course of nearly two and a half years. Through her efforts, it’s expected that 99.9 percent of Parler’s content was captured, including the metadata of every public, private, and deleted video. While most social media platforms have policies in place to both secure and delete a post’s sensitive metadata after the content is uploaded, @donk_enby’s research proved that Parler had not enacted such cybersecurity procedures and placed all its users at risk.
Contained within an unprotected Amazon Web Services (AWS) server, this information not only revealed basic information about each video and its owner, it also provided exact GPS coordinates of where the individual was located when posting said footage. By handing this information over to criminal investigators, @donk_enby’s efforts not only shed light on one of the largest social media breaches to date, but also gave enough evidence to track down and arrest key suspects that played a role in the Capitol’s attack.
Why Did Apple, Google, and Amazon Remove Parler?
Two days after the events in Washington D. C. took place, both Apple and Google provided Parler CEO, John Matze and his team with 24 hours to delete content containing violent and illegal activity and provide a plan for future moderation or it would face removal from the app stores. The following day, on January 9, both tech giants subsequently removed Parler from each of their respective mobile stores. With a large portion of the U.S. population relying on smartphones as a primary means of accessing the internet, Parler’s removal from the Apple App Store and Google Play Store did not bode well for its future success. But the final blow for the social media platform came later that day, when Amazon removed the company from AWS for violating its terms of service; leaving the Parler development team without a cloud service to house their app.
Parler Returns to Apple App Store
Apple recently said in a statement that a revised version of the Parler app would be relaunched to Apple users at the end of April. There have been substantial conversations between Apple’s App Review Team and the Parler team to bring the app into compliance with the guidelines of the App Store. While the specific changes that sparked Apple’s previous decision are unclear, Parler is suspected to have made updates to its content moderation policy to ensure there’s a way to safeguard “objectionable” material from getting posted. This will be the first time the app has been made available since February 2021 and provides Parler’s leadership with not only an opportunity to rebuild its userbase, but also foster a more positive narrative of its brand reputation.
That said, February’s incident wasn’t the first time the struggling social media platform faced cybersecurity issues since it gained traction in late 2020. In November, Parler had a prior security flaw in its AWS server; with the passwords, photos and email addresses of users being leaked across the web. But despite Parler’s negligence for properly securing user data on multiple occasions, it’s not the only social media platform to face serious AWS data breaches in recent history. Over the last seven years, Facebook has seen over 597 million accounts compromised, and that number has only grown with Facebook’s acquisition of Instagram. On May 20, 2019, a public AWS database containing over 49 million Instagram user records was found online. More specifically, this unsecured database contained the bio, profile image, number of followers, location, email address, and phone number for each of the compromised accounts.
How to Secure Your Social Media Accounts
But as breaches like the ones discovered in both Parler and Instagram become more common, what can you, the active user, proactively do to mitigate the fallout from a data leak?
Switch from Passwords to Passphrases
On average, an eight character password can be cracked in less than two and a half hours. Instead of relying on something that is short and easy to remember, such as a pet’s name, try creating a passphrase that includes a combination of 24 letters, numbers, and special characters. To learn more about the benefits of passphrases, click here.
Use Multiple Passphrases
While it may seem harmless, using the same passwords across multiple accounts creates a serious cybersecurity risk. Because two out of three people recycle the same password across multiple accounts, when a hacker obtains a password through a breach, they will then attempt to use that same password to access other accounts, such as ones tied to financial services. Therefore, it’s important to create a unique passphrase for each account and store them in a password manager for safe keeping.
By using a password manager, an individual can store all their passwords in one secure location; only needing to remember a single master password. While there are a variety of these services available, Rocket IT has put together a guide to walk you through the selection and installation process.
Deploy Multi-Factor Authentication
Multi-factor authentication is a term used to describe an application that requires a person attempting to login to an account with two forms of identification. While the first method of identification is typically something the individual might know, such as a password, the second layer of security requires the individual to have something in their possession, such as a smartphone. Most commonly, MFA services rely on facial recognition, static PINs, texted codes, or the acceptance of push notifications to ensure the individual attempting to log in is legitimate. For more information on MFA, Rocket IT has prepared a full article on its use cases here.
Be Aware of Location-Based Services
As seen in the Parler data leak, apps can collect and store an individual’s location without letting them know how it will be used. And although some apps require location-based services to be on for the app to function, it’s best to only have those setting enabled while the app is currently open. To check if an app is using your location on an iPhone, head to Settings, scroll down to Privacy, and select Location Services. Here, you’ll be provided with a list of all installed applications. Once there, find the app in question, tap on it, and change the setting only allow Location access while using the app.
Social media services are notorious for collecting the information of their users. And although the heads of these companies argue that the data is kept safe and not sold to third parties, simply trusting that a multi-billion-dollar CEO has you best interest at heart is a leap of faith. Instead, Rocket IT encourages you to implement the security measures mentioned above not only on your personal, but across your network of business devices as well. To learn how these password security initiatives can be implemented company-wide, give Rocket IT a call at 770-441-2520.
Related Posts
Subscribe to Rocket IT's Newsletter
Stay up to date on trending technology news and important updates.

Find out if Rocket IT is the right partner for your team
Claim a free consultation with a technology expert.










