
Instagram’s Recent Breach: How to Protect Your Data

When developing a relationship with another individual, it’s fair to say that some time is needed before you begin to share private information with the other party. Once you feel assured that the individual can be trusted, you’re more likely to provide them with some insight into your personal life.
That said, many social media sites expect a user to completely forgo this exploratory process, taking it upon good faith that the developers of the site have created an environment in which this information can be shared securely. Unfortunately, this is not always the case; and with information on expansive data breaches continuing to surface, users may quickly discover that their perceived trust with these organizations is easily violated.
How Could This Possibly Occur?
Before diving too deeply into this subject matter, it’s important to first explain what a data breach truly entails. According to Trend Micro, “a data breach is an incident where information is stolen or taken from a system without the knowledge or authorization of the system’s owner.” Now, you may be asking yourself: how can an organization go so long without noticing its information is being siphoned from underneath its very nose? While the answer to this question is quite complex, there’s a few varying methods these attacks can be attributed to.
- Insider Leak – A once-trusted individual (or former employee) steals the information, typically selling said data to the highest online bidder.
- Exploits – A hacker actively scans the structure of an organization’s network, hoping to stumble upon a vulnerability that gives unauthorized access to a system. Once inside the network, the individual is able to secretly reroute where information, such as consumer credit card information, is sent. Picture this tactic similar to that of a credit card skimmer thieves place on ATMs.
- Physical Theft – Theft does not always occur from within the digital realm. Unattended laptops, portable harddrives, desktops and other physical properties without proper encryption can be stolen to gain consumer information.
- Human Error – As with any potential issues, a simple human error can have catastrophic results. In regard to data breaches, a developer may misconfigure access controls, accidentally exposing data when it was meant to be private.
That’s a Lot of Compromised Accounts
While it seems like almost every major organization has experienced some level of data breach in recent years, none have come close to the public relations nightmares that continue to plague Facebook’s team. In the past six years alone, Facebook has seen over 597 million accounts compromised; and now that the social media giant has acquired Instagram, this number has steadily grown. On May 20, 2019, security researcher, Anurag Sen, discovered a metaphorical gold mine of Instagram user data. By casually browsing Amazon Web Services’ cloud platform, Sen came across a public database containing over 49 million Instagram user records – including each individual’s bio, profile image, number of followers, location, email address and phone number. Although the owner of this database was originally left undisclosed, the online technology news publisher, TechCrunch, was quick to jump on the scent. Within a matter of hours, the news organization tracked the database back to the perpetrator: Chtrbox, a Mumbai-based social media marketing firm that pays influencers to share advertised content via social media. While Chtrbox claims it uses autonomous screen-scraping technology to scan the information of publicly viewable accounts in an effort to locate popular influencers, this response doesn’t explain how the organization gained access to the private email and phone number of each user.
Although the database was quickly removed after its discovery, the wake of this event doesn’t bode well for the success of Facebook’s newest initiative, Libra – a cryptocurrency the parent company plans to soon integrate into each of its affiliated social media platforms, including Instagram.
Placing Control in the Hands of a User
With these organizations now setting their sights on the financial banking industry, each of these platforms is bound to experience an upward trend in cybersecurity risk. As these threats continue to rise, standard users of these platforms will inevitably find themselves searching for useful methods to protect their accounts and the information contained inside. To lend a helping hand in this expansive search, Rocket IT has included some effective measures individuals can incorporate into their current social media practices.
- Set account to private.
- While many Instagram users enjoy receiving affirmation for the content they post, some individuals prefer to keep their images private. In doing so, screen scraping technology, such as the one deployed by Chtrbox, have a more difficult time pulling your information from publicly accessed sites.
To set your account to private, first navigate to your Instagram profile. Once you’re there, tap the three bars in the top-right corner of the screen. At the bottom of this menu, you should see the option to access your profile’s settings: click that. From this sub-menu, scroll down and select Privacy. Under the section labeled Connections, you should see a setting titled Account Privacy. Tap that and swipe the button to toggle your account’s privacy.

- Switch from passwords to passphrases.
- Fortunately, Instagram’s most recent data breach did not reveal the passwords of users. That said, it did give the general public (and criminals) easy access to the email addresses of many community members. With this information in hand, the job of a hacker just got that much easier. Now, the cybercriminal can focus his or her attention solely on cracking the password of an unsuspecting user.
Fortunately, creating a strong password goes a long way when it comes to mitigating this risk. Instead of simply using your pet’s name, try implementing a 16-character passphrase containing a mix of letters, numbers and symbols. To generate a passphrase that is both complex and easy to recall, consider making your password reflective of a current goal. For example, “LoseTenPoundsBy2020!” contains all the characteristics of a strong password. To learn more about the benefits of using passphrases, click here.
- Use multiple unique passwords.
- Should a data breach leave your password exposed, it’s important to ensure that any negative effects are contained within that one account. Once a hacker both your email and password on file, he or she is likely to use those login credentials in an attempt to access other online portals you may be affiliated with. Therefore, it’s crucial that individuals use a unique password for each of the accounts they create.
While, upon first thought, you may doubt your ability to keep track of all these passwords, know that password manager makes the process quite easy. By using one of these services, an individual can store all their passwords in one secure location; only needing to remember a single master password. While there are a variety of these services available, Rocket IT has put together a guide to walk you through the selection and installation process.
- Incorporate two-factor authentication across online accounts.
- Depending upon the severity of the data breach, both the email addresses and passwords of users may be compromised. If this is the case, having two-factor authentication linked to your Instagram profile, email, and online banking can thwart a hacker’s attempts, regardless if they have your information readily available.
For reference, two-factor authentication is an application that asks a user for another form of identification after entering the correct login credentials. While this guide explains the different methods available to consumers, Instagram has its own two-factor authentication integrated into the platform. To access this feature, first navigate to your account’s settings. Once there, tap security and then choose two-factor authentication from the sub-menu. Instagram will then walk you through the installation process, while also giving you the option to incorporate the functionality of many well-known two-factor authentication services.

- Monitor your account activity.
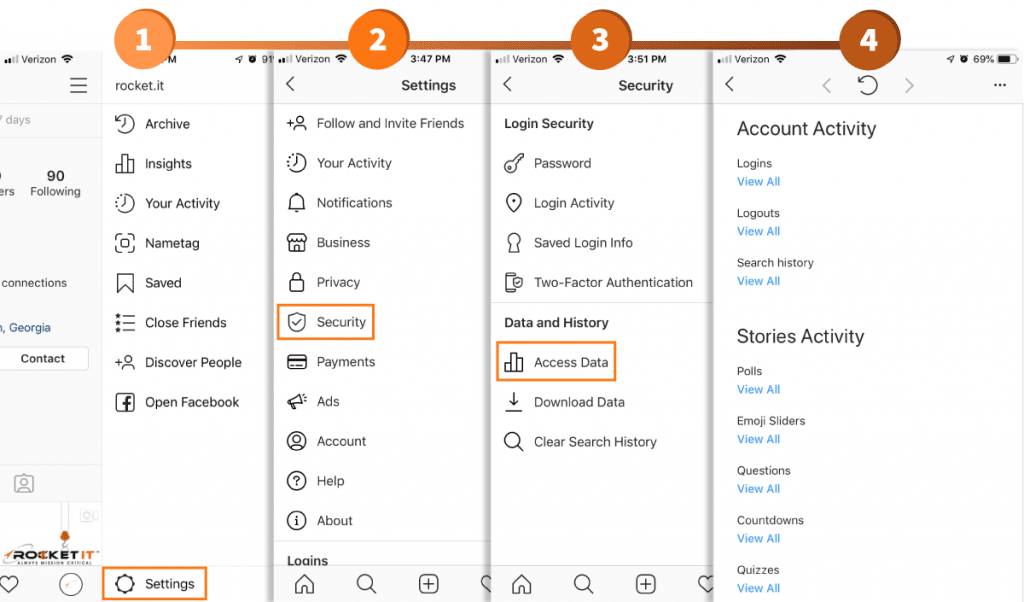
- Similar to how online banking allows consumers to monitor their accounts for fraudulent charges, Instagram’s Access Data setting gives users the ability to track logins, logouts, search history, and other insightful analytics. In particular, this comes in handy should you believe your account information has been breached.
To view this information, navigate to your account’s settings and select security. From the new menu that appears, select Access Data, under the Data and History tab.
- Initiate a force logout for all devices.
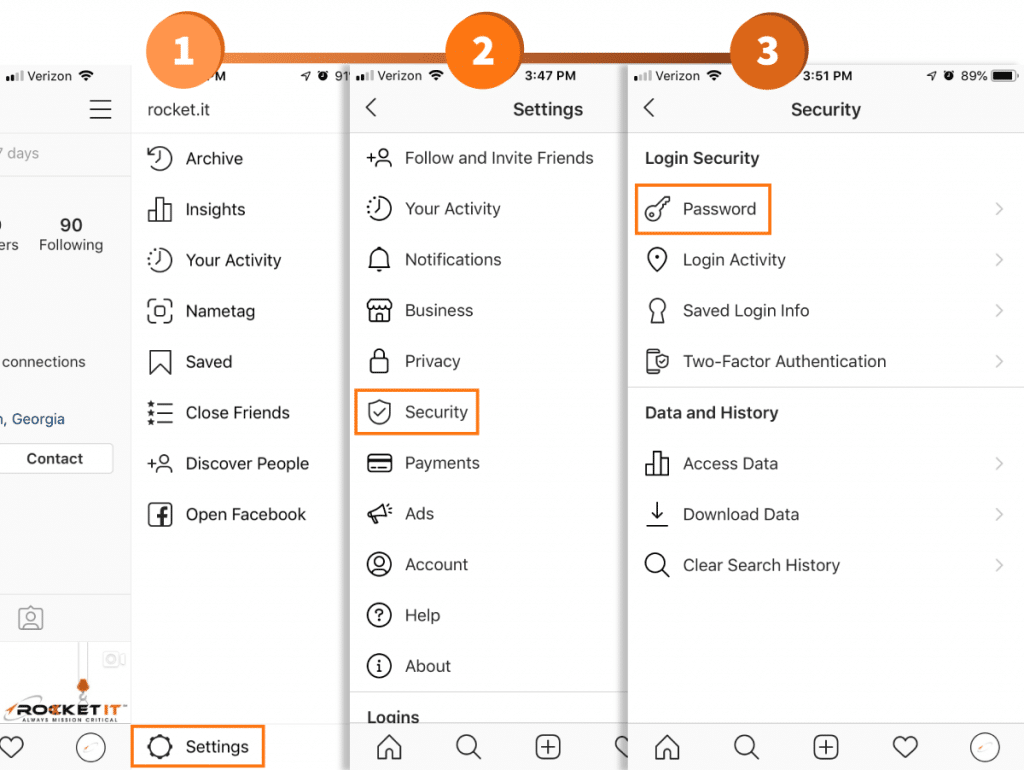
- If you notice suspicious activity after using Instagram’s Access Data feature, it may be beneficial to force all devices connected to your account to log out. While Facebook has this feature built into the platform, Instagram has yet to release a straightforward process to accomplish this task. That said, by changing your password, all devices signed into your Instagram account will be immediately kicked offline, only regaining access if they have knowledge of the new password.
Completing this objective is pretty easy. Simply access your account’s settings, navigate to Security and tap Password under Login Security.
- Review authorized third-party apps.
- Many times, third-party mobile applications will request that individuals link their social media profiles to the service. By doing so, users of these third-party applications are promised faster login times, more functionality, and a variety of other features. While these incentives provide the individual with some immediate benefits, users that sign up for these services increase the chances of their information being exposed via a data breach. Simply put, accepting the terms and conditions of many third-party applications gives the developer the right to collect and sell the user’s data. In return, if the development team has not placed a significant emphasis on its security measures, the information of its user-base is left sitting ripe for the picking.
Unfortunately, checking to see if any third-party applications have access to your information requires the use of a desktop or laptop computer, making the process slightly less convenient than some of the other security measures mentioned thus far. Once you’ve logged into your account via https://www.instagram.com/, navigate to your profile. Similar to how your settings are accessed via a mobile device, click the gear icon next to your profile’s username. From the pop-up menu that appears, select Authorized Apps. If any items should generate on this list, take the time to carefully re-read the terms and conditions each application, removing any that do not meet your perceived security criteria.

- Mindfully use location-based services.
- Like the data gathered by third-party developers, Instagram’s location-based features continuously keep tabs on the whereabouts of a user. While, for the most part, this information is only released if an individual publicly includes it in one of their posts, this isn’t to say that a backlog of this data can’t be acquired through a data breach. For high-profile individuals, a breach of this nature would allow others to draw conclusions of their daily routines, making them susceptible to the motives of stalkers.
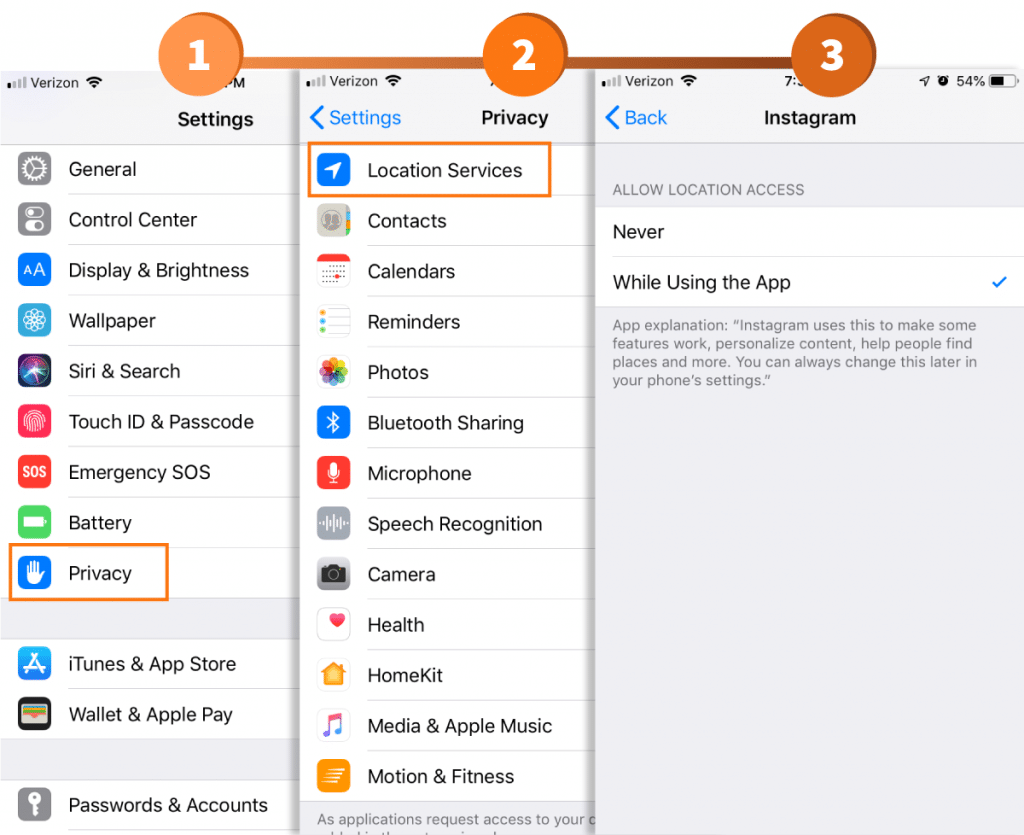
If you happen to be an iPhone user interested in altering this setting, navigate to your smartphone’s settings. Once open, access the phone’s Privacy settings, and select Location Services. After each application has populated on the list, scroll down until you find Instagram. By selecting this setting, you’ll then be able to define whether the application can track your location. That said, be mindful that location-based services do happen to make finding information on nearby establishments quite an easy process.
Mitigating the Risks
While the developers of Instagram, Facebook and other social media platforms have recently found themselves being grilled for improperly securing the data they collect, the benefit of these breaches is that more control is being placed in the hands of consumers. By effectively leveraging both the security tools provided in the apps themselves and the smartphones that encompass them, users can ensure they’ve taken the necessary precautions to mitigate the risks associated with these all too common data breaches. That said, some security measures, such as those pertaining to password protocols, have an application far outside that of just social media. To learn how the password security and management initiatives mentioned in this article can be implemented on a company-wide scale, Rocket IT encourages you to give us a call at 770-441-2520.
