Technology
Chipotle Marketing Hacked to Send Phishing Emails | Sync Up With Rocket IT
Hailed by many fast-food connoisseurs as the best place for a to-go burrito, beloved restaurant chain Chipotle is making headlines as cybercriminals recently hacked the organization’s email marketing account and used it to send customers phishing emails.
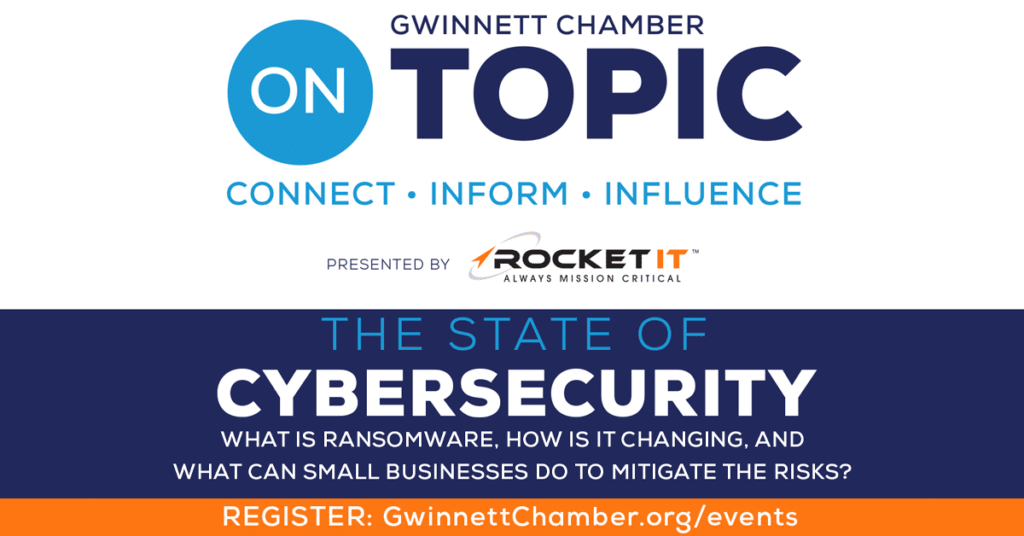
Read MoreState of Cybersecurity | What is Ransomware?
What is ransomware, how is it changing, and what can small businesses do to mitigate the risks?
On August 18, Rocket IT and the Gwinnett Chamber of Commerce are teaming up to provide On Topic attendees with a deep-dive into some of 2021’s most notorious hacks to date.
Read MoreIntel’s Solution for the Semiconductor Crisis | Sync Up With Rocket IT
With 2020 forcing businesses to close storefronts and social gatherings becoming restricted, people have leaned into technology for work and relaxation more than ever before. In turn, we’re facing a global shortage of semiconductors, making it nearly impossible to purchase new tech when it launches. Here’s how Intel plans to solve that issue.
Read MoreWhat’s New in Windows 11? | Most Exciting Features
Six years after Windows 10 hit the market, Microsoft has finally unveiled its new operating system, Windows 11. Expected to launch in late 2021, Windows 11 will still provide users with access to the power and security they have grown accustomed to while also offering access to new features designed to improve productivity.
Read MoreIs Your Phone Listening In? | Sync Up With Rocket IT
Think your phone is listening in on your conversations while it sits quietly in your pocket? That thought might just be as a recent investigation from the Washington Post claims that the smartphones of 37 human rights activists and journalists were potentially hacked using wiretapping software.
Read MoreShould Tech Repairs Void Your Warranty? | Sync Up With Rocket IT
For years, popular tech manufacturers have had a stranglehold on the repair market, with costly service fees forcing many individuals to abandon their older devices and purchase updated models. But as of last Friday, the United States government is seeking to put a stop to this trend and restore power to the consumer.
Read MoreCase Story | Multi-factor Authentication
While many businesses race to implement a variety of security applications across their networks, the real vulnerability lies at the employee level. And with 95 percent of breaches occurring from human error, here’s how one organization drastically reduced their odds of attack through multi-factor authentication.
Read MoreThe Biggest Ransomware Hack to Date | Kaseya | Sync Up With Rocket IT
Over the weekend, cybercriminals pulled off the largest ransomware hack to date. And while the potential $70 million payout for these criminals may be alarming on its own, the fallout from this event serves as a warning sign for even the most well-versed of cybersecurity experts.
Read More700 Million LinkedIn Accounts Leaked | Sync Up With Rocket IT
Fresh off the trail of its record-breaking data leak in April, LinkedIn is back in the hot seat as the information of 700 million individuals have popped up online.
But what does this invasion of privacy mean for the future of LinkedIn and its massive user base?
Read More