
Case Story | Multi-factor Authentication

There’s no denying that digital threats have become quite advanced over the last few years. From ransomware to keyloggers, hackers are eager to find new ways of infiltrating unprotected businesses. But despite implementing innovative security applications across business networks, the real vulnerability lies at the employee level. 95 percent of breaches are initiated by human error, and compromised passwords are responsible for 81 percent of hacking-related incidents.
You’re in the Architecture, Engineering, and Construction (AEC) Industry
Imagine you’re the leader of a financial team at a construction company that specializes in designing, building and financing a multitude of different projects. You manage a team that work with clients in a variety of industries, ensuring payments for elaborate projects are processed in a timely manner. These developments, which tend to be quite pricy and often cost millions of dollars, provide new, functional facilities for the communities in which they are built. Because of the large price tag and the potential impact at stake, you know just how important it is to properly manage funds to protect your organization and your stakeholders.
Risks in Your Sector
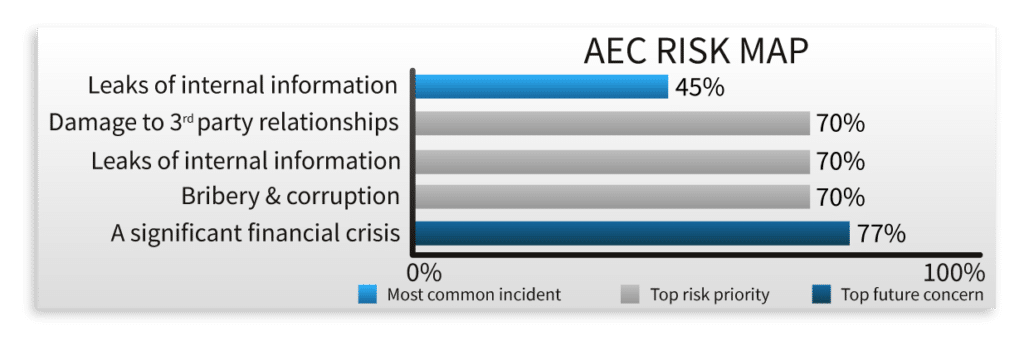
Like 70 percent of your peers in the AEC industry, you worry that your organization will be the victim of an internal information leak. As a result of this fear, your organization has implemented some of the most innovative technologies available on the market. From modern anti-virus solutions to advanced firewalls, the business has exhausted its resources seeking out measures to protect not only your team, but your clients and vendors. But what you don’t know is, that despite your organization’s best spending efforts, these technologies do little to mitigate the risk of breaches caused by human error.
“While many businesses are spending millions of dollars on technology annually to protect their digital assets, human error remains the number one cause of these breaches,” said Rocket IT VP of Services, Eric Henderson.
Back in January…
On a brisk morning in January, a member of your team opens an email that appears to be an account verification request from Microsoft. They click the link, quickly enter their login credentials, and think nothing of it as they continue about their day. Six months pass and it’s now summer, your busiest season of the year. Each day, the inboxes of your direct reports are flooded with messages regarding inbound and outbound payments. And while your team is doing their best to sort through these emails, what you don’t know is that an unauthorized individual is secretly doing the same. Back in January, the fraudulent account verification your team member completed provided a cybercriminal with access to their Microsoft account, and they’ve been collecting the emails from each client contact ever since. Like 45 percent of AEC firms, you’ve become the victim of a serious data leak, and you’re completely unaware.
As the chaos of your busy season ramps up, the team member with the infected account begins sending out a multitude of payment requests to clients. With each new invoice sent, the cybercriminal follows up with a secondary email, notifying clients that the payment routing instructions included in the previous email are incorrect, and that fees should be wired to a new bank account instead. To guarantee that these emails go undetected, the cybercriminal carefully ties a fake email domain to your team member’s real account, ensuring the emails don’t appear in their sent folder. Then, by implementing a custom rule in Outlook, the cybercriminal routes all client replies to a hidden folder and marks the contents as read to hide their visibility.
Over the next few days, you notice that you’re missing $30,000 in funds from a high-profile client that typically submits payments on time. Frustrated, you ask a different team member to send another invoice. You quickly hear back, with the client stating that the payment had successfully been delivered. Puzzled, you quickly check your accounts and notice you’re missing another $38,000 in payments from smaller clients. Upon reaching out, your confusion quickly turns to fear as each client relays a similar story.
You Contact Rocket IT For Help
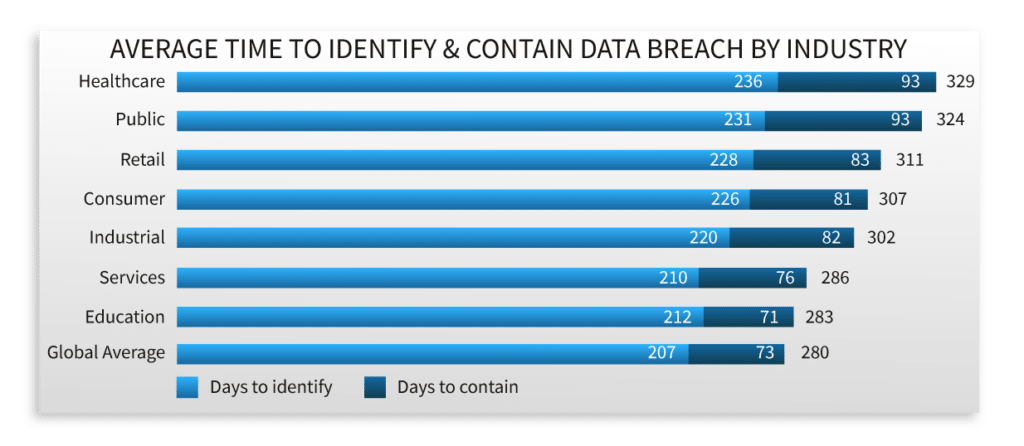
With $68,000 in capital at risk and the number growing, you immediately call Rocket IT to help secure your accounts. You suspect that your organization has been hacked, but seeing as the average time to identify a breach is 280 days, you’re unsure of when or how this could have happened.
The Rocket IT team conducts a thorough investigation of your network, taking note of all email users, systems, and potential points of weakness in your organization. They spot a couple of red flags, the most prevalent of which is a lack of policies requiring team members to secure their Microsoft 365 accounts with Multifactor Authentication (MFA) enabled. After taking a closer look, the engineers find that at least one of your users has an unsecured email account and their credentials appeared in a data leak about six months prior.
A Step in the Right Direction
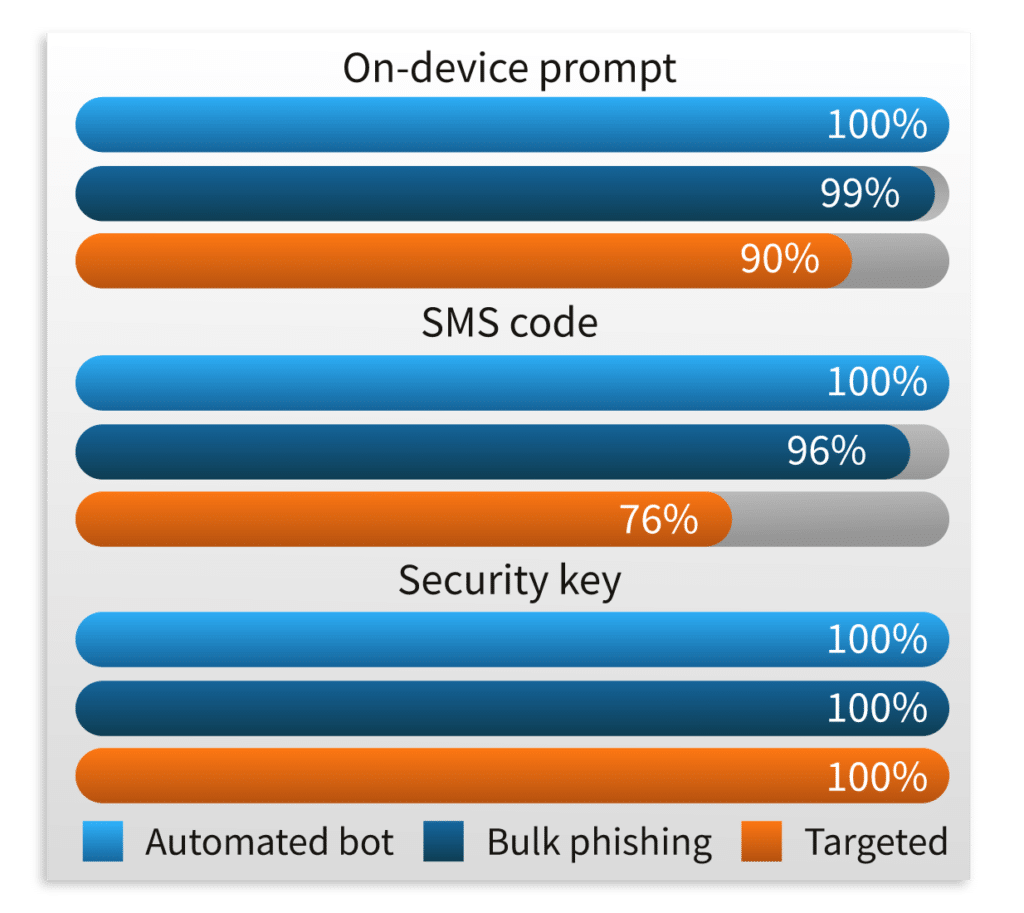
As you sort out your invoice payment issues with your cybersecurity insurance provider, you give Rocket IT the green light to upgrade your network security. Rocket IT gets right to work, enabling MFA for every team member’s Microsoft 365 account and your organization’s VPN. By adding this low-cost layer of security, your organization is taking a step to prevent 100 percent of automated attacks, 99 percent of phishing attacks, and 90 percent of targeted attacks on your Microsoft 365 assets.
Noting that MFA is available on a plethora of modern business applications, Rocket IT helps you create a policy to ensure this layer of security is added whenever the option is available. Furthermore, to ensure similar invoice fraud does not occur in the future, you instate a procedure that requires online payments to be accompanied by a phone call with voice confirmation. For businesses, staying aware of new vulnerabilities, improving login security, and maintaining preventative safety measures can provide protection against attacks. To move your business in the right direction and deploy MFA across your entire network, give Rocket IT a call at 770.441.2520.
