Technology Resolutions to Consider for the New Year
Each January, one in four people start the year with a set of hopeful resolutions. And while hitting the gym can help some individuals achieve their goals, for those hoping to improve the health of their organizations, investing in technology can have a huge impact. That said, finding new ways to leverage technology can be daunting, so Rocket IT has a few suggestions you can take to put your best foot forward when entering the new year.
Resolution One | Backup Your Data
Everyone has been there. You’re tirelessly working on a project when all of a sudden, your program crashes. If you haven’t recently saved your work, all that effort goes down the drain and you’re left with no other option but to begin again from scratch. Simply put, there’s no effective way to predict when software or hardware will fail. It can happen at any time; and when it does, it’s only natural to expect some file corruption or data loss. Fortunately, if you have a routine backup procedure, this threat poses far less risk.
Benefit | Backups Reduce Long-Term Costs
Not only does a properly implemented backup policy give you and your organization a safety net, but it can also reduce long-term costs for an organization. Whereas attempting to recover lost files without any standardized backup method can require an excessive amount of time and range dramatically in price; taking proactive measures can provide business leaders with a known cost to budget for.
Resolution Two | Move to the Cloud
So, let’s say you’re already backing up your data, where’s the most secure place to store it? For many people and organizations, cloud services offer a viable solution. Not only does incorporating cloud services into your network boost your data’s security, it also provides your business with a more flexible workplace.
Benefit | Cloud Storage Offers Flexibility
For example, let’s imagine you have a giant project you need to backup, but your on-site server is nearly out of space. Rather than waiting for hard drives to be bought and installed, cloud services allow you to scale your storage space to accommodate large files in just minutes.
Additionally, for businesses that are running hybrid or remote operations, cloud storage offers a simple way to give employees access to information outside of the office. In turn 59% of businesses that deploy cloud services are likely to see immediate productivity benefits. That said, not all cloud service plans are built the same and what might work for one business, might not works for yours. Therefore, it’s important to talk to your IT provider before making the leap to the cloud.
Resolution Three | Deploy a VPN
Despite how great cloud services can be in terms of flexibility and security, sometimes they aren’t the sole solution for businesses that need more control over their virtual environments. In turn, hosting a private server within the office space may give said organization a more advanced environment to do things, like building and running custom applications. While this option is great for those individuals working within the office, when it comes to accessing a private server remotely, you’re going to need a virtual private network, better known as a VPN.
Benefit | VPN’s Boost Network Security
In addition to simply connecting remote employees with on-premise servers, a VPN ensures said connection is secure. Therefore, VPNs greatly mitigate the chance that sensitive information can be accessed by individuals with malicious intent. Furthermore, because no one likes being watched while online, VPNs disguise your IP address, making it more difficult for hackers to steal your valuable information.
Resolution Four | Update Your Tech
We’ve all been there. You’re diligently working when a notification to update and restart your PC appears. Rather than dismissing the notification until a later time, Rocket IT recommends installing these updates as soon as possible. If left uninstalled, devices are left open to attack, putting both personal and organization data at risk.
Benefit | Updating Software Patches Vulnerabilities
In 2021, around 18,500 software vulnerabilities were discovered by researchers, with many research teams averaging 50 discoveries per day. Once discovered and published by researchers, it’s only a matter of time before hacking groups begin to take advantage of said vulnerabilities. As a result, software developers take these warnings seriously, create security patches, and push them out to their user-bases as quickly as possible. By hiring and IT provider to quickly apply these software patches across your company, you’re doing your part to ensure hackers can’t exploit these vulnerabilities to gain access to your network.
Resolution Five | Create Password Security Policies
While keeping your software updated can greatly boost the security of your business network, four out of five breaches occur from weak or stolen passwords. And while something as simple as creating a company-wide password policy can greatly reduce the risk, what should you include?
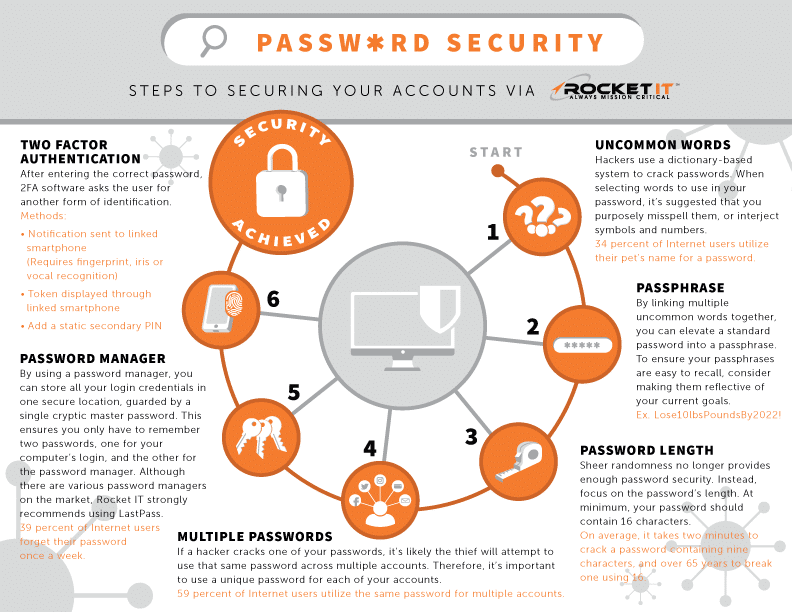
Benefit | Password Policies Easily Prevent Breaches
First and foremost, make sure you ensure your entire team creates passwords that are 16 characters long and a combination of letters, numbers, and special characters. In the spirit of the new year, Rocket IT suggests creating passwords reflective of personal goals, such as Lose10lbsby2023!.
Next, you’re going to want to ensure everyone is using different passwords for each of their accounts. This ensures that if one password is cracked, they don’t have access to multiple accounts.
With that said, asking employees to create different passwords for each account means it will quickly become difficult to remember those login credentials. Therefore, it’s important to use a password management tool; essentially allowing a user to store all their login credentials in one secure location, guarded by a single cryptic master password.
Finally, when it comes to implementing a strong password policy across a team, multi-factor authentication is crucial. Better known as MFA, the authentication program asks the individual to provide additional identification, such as a one-time PIN or code, once a correct password is entered.
By asking an IT provider, like Rocket IT, to deploy these policies company-wide, business leaders can sleep easy knowing they’ve reduced the likelihood of a data breach by 81%.
Resolution Six | Implement Phishing Testing
Despite many hackers finding success in cracking simple user passwords, thieves may also use phishing scams in an attempt to access your accounts. For those unaware of what phishing entails, think of this as an attack in which cyber criminals pretend to be a reputable person or organization in hopes of stealing passwords, personal identification, or banking information.
While these attacks can be delivered using a variety of sources, phishing scams are most commonly sent via email. In turn, opening a phishing email may reveal a message that appears legitimate, but often contain malicious attachments or fraudulent payment requests.
Benefit | Phishing Tests Train Employees
Many IT providers, including Rocket IT, offer clients phishing prevention training to detect users that may be prone to clicking questionable links. Because it’s difficult to decipher authentic emails from phishing scams, the training tests users by sending harmless, yet still bogus, emails. In return, the administrator of this test is notified when users click the content contained within the message. Individuals that click are then placed on a list and required to undergo additional training on the subject.
Resolution Seven | Create a Departure Guide
Although the goal of most business leaders is to invest in employees and provide a long-term workplace, it’s often easy to notice when a relationship isn’t working out. And while parting ways with a team member is a tough pill to swallow, an employee departure guide can alleviate some of the pressure.
Benefit | Departure Guides Streamline Technology Offboarding
When it comes to creating a departure guide, there are three key areas that need attention: cloud data, subscriptions, and email accounts. When implementing a cloud storage policy across an organization, it’s important that team members make a habit of storing company-owned assets in a centralized location. This ensures that when an individual is removed from the team, their rights to retrieve this sensitive information are revoked, while other users retain access to that data.
Next, it’s crucial that this employee departure guide includes a method to track user login credentials to business-owned accounts. Taking this step ensure your team isn’t locked out of important accounts when an individual departs from the group.
Finally, to preserve a steady flow of communication in a previous team member’s absence, business leaders must decide what steps to take with the user’s email account. In particular, questions pertaining to email forwarding, inbox history, and account deletion should be addressed. To assist in determining what should be done with the individual’s inbox, Rocket IT offers readers an online employee departure assessment.
New Year. New Opportunities.
While this article presents some food for thought, defining the technology-based resolutions for a business’s success lie on the shoulders of its leaders. By taking the time to reflect on an organization’s current technology environment at the beginning of each year, leaders can ensure a team builds healthy tech habits for years to come. For more information on how Rocket IT can help with your goal setting, give us a call at 770.441.2520 to speak with a member of our team.
Related Posts
Subscribe to Rocket IT's Newsletter
Stay up to date on trending technology news and important updates.

Find out if Rocket IT is the right partner for your team
Claim a free consultation with a technology expert.