New Zoom Vulnerability | Zero Day Security Risk
With over 467,000 business customers, Zoom is hailed for its simplicity and easy user interface. But with this simplicity comes some vulnerabilities, as attackers have frequently exploited the security shortcomings of the software.
How Was Zoom’s Vulnerability Discovered?
A new Zoom security vulnerability has been found by two cybersecurity professionals, Daan Keuper and Thijs Alkemade, during the Pwn2Own Competition organized by the Zero Day Initiative. The competition challenged ethical hackers to find new vulnerabilities in commonly used software to mitigate the risk of information being stolen and sold to cyber criminals.
Through this hacking competition, the researchers discovered three vulnerabilities and combined them to remotely control another test computer. To accomplish this feat, it was found that the attacker first sends the victim a request to be accepted as a Zoom contact or they gain access to an account that’s listed under the victim’s same organization while a Zoom call is live. Once one of these conditions are met and the code is executed remotely by the hacker, the cybercriminal is free to open any program they wish on the victim’s computer.
What is a Zoom Zero-Day Vulnerability?
A zero-day vulnerability is a security flaw that’s unknown by developers of a software but could potentially pose a risk to its users. These vulnerabilities tend to be rather difficult to find and often require hours of researching. Because of this, major developers offer cash rewards to those researchers who both find the vulnerability and bring it to the attention of their team. In the case of this discovery, the researchers in question received $200,000 for their efforts.
That said, once a vulnerability is found, the work is not done. Exploitation occurs between the time a vulnerability is discovered and the time when the resolving update is released. In general, the longer it takes to find and resolve a vulnerability, the more likely users will be at risk of attackers writing malicious code to gain remote access to their computer and network.
Zoom’s Response to the Hack
Zoom hasn’t patched the critical security issues yet since the company has 90 days to produce a fix for all vulnerabilities reported before details are released, as stated in rules established by Pwn2Own. That said, the researchers were able to reveal that the vulnerability can only be exploited on the Windows and Mac Zoom apps and does not impact the browser version of Zoom.
Although the Alkemade and Keuper discovered the flaw in only two days, it’s expected that it may take Zoom months to apply a fix . Specifically, more testing is needed to understand if the attack affects the iOS and Android app versions of Zoom.
In the meantime, the aim is to have responsible disclosure and only reveal details when a patch is readily available to protect end users, effectively preventing attackers from wreaking havoc on unsuspecting Zoom calls.
Previous Zoom Vulnerabilities
Within the last year, Zoom has faced several holes in its security, many of which were exploited at the beginning of businesses shifting to remote operations. The most recent vulnerability is just one of the numerous problems that have put users of the video calling service in harm’s way.
In March 2020, a vulnerability, coined Zoombombing, let hackers take advantage of public meetings to share explicit audio or imagery with entire audiences of people. In addition to sharing this content, scammers also took advantage of the situation, using the exploit to share malicious links in chat; sending the victims that clicked to fraudulent websites that could potentially install malware, steal login credentials, or conduct various other attacks.
While Zoom has since taken action to mitigate the risk of Zoombombing, the company had to completely reevaluate its password policy for meetings and implement new default security measures. In turn, the act of Zoombombing is now recognized as a crime and states have started prosecuting those that violate the law.
But Zoom’s questionable security isn’t limited to Zoombombing. Last year, Zoom’s encryption policies faced scrutiny by the Federal Trade Commission as it was found that Zoom was falsely promoting ‘end-to-end, 256-bit encryption’ and instead providing a lower level of security. Through this investigation it was also found that Zoom incorrectly told customers that recorded meetings stored on its servers would immediately be encrypted, giving users a false sense of security. In turn, these were critical contributing factors that led several school systems to ban the software completely in 2020.
Zoom also suffered backlash in 2019 when it was found that the developer was secretly installing web servers on Mac hardware. While this decision was meant to allow Zoom to automatically initiate updates to their platform, once hackers manipulated the feature, it inevitably resulted in cybercriminals spying on devices and, in some circumstances, taking remote control over Mac computers.
A Necessary Evil….Or A Thing of the Past?
While Rocket IT strongly suggests that individuals in need of a secure video conferencing solution consider using Microsoft Teams instead of Zoom, it’s likely that Zoom’s wide rate of adoption will mean that you’ll need to use the platform at some point in the future. Because of this, Rocket IT has compiled some general tips and practices to make sure you are being as safe as possible when using Zoom.
Use Zoom’s Web Browser Version When Possible
First, only join Zoom meetings through your web browser. By bypassing the desktop application, you can also bypass that sneaky web server acting on your behalf. A bonus benefit is that the web browser gets security enhancements quicker than the installed app and it’s limited in how it can ultimately affect your device.
Require a Password for Zoom Meetings
Second, make sure all meetings are protected by requiring participants to join with a password. This will prevent most Zoombombing and ensure the participants joining your meeting are the correct individuals. It is advised to schedule meetings via the Zoom web portal to ensure you have total control/
1. Once logged into the web portal, navigate to “My Account” and select “Meetings” from the left navigation menu. Enter the topic, description, date, time, and duration as you normally would.
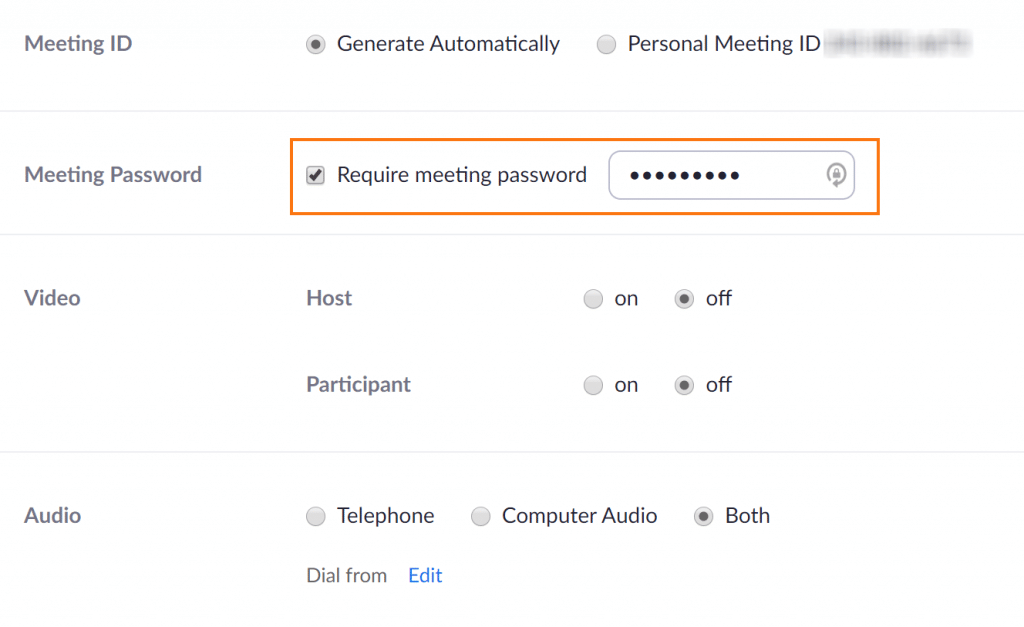
2. Under the “Meeting ID” setting, make sure “Generate Automatically” is selected. This will assign new, unique IDs for each meeting you host instead of your personal meeting ID being used repeatedly.
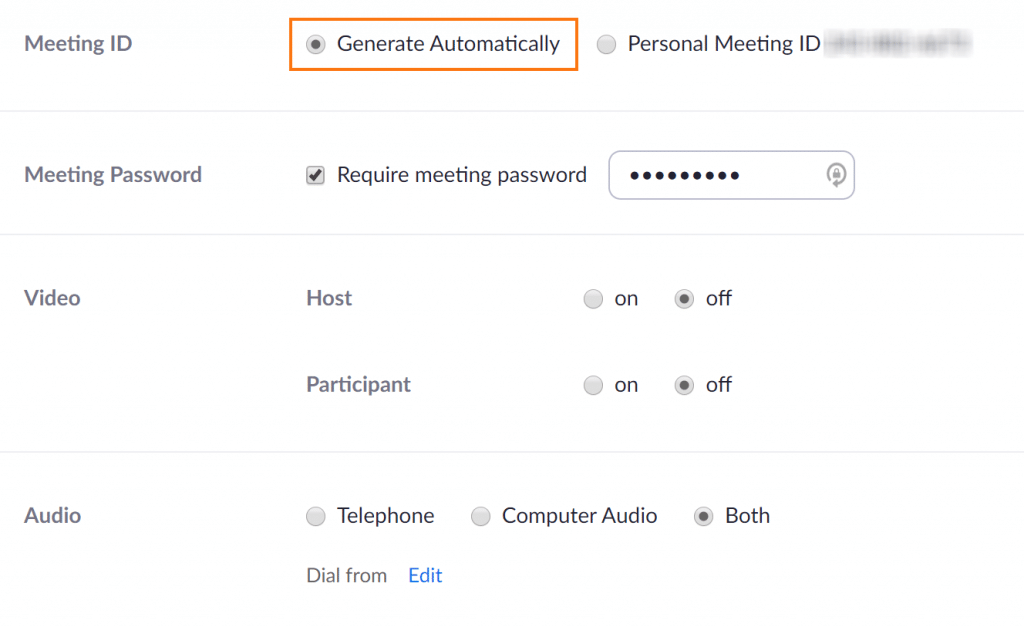
3. Next to “Meeting Password,” the option to “Require meeting password” is selected by default. Rocket IT recommends keeping this setting turned on and changing the password for each meeting. For steps on creating a strong password, check out this article on passphrases.
Finally, make sure Multifactor Authentication (MFA) is set up for your Zoom account. MFA requires an individual to provide not just one, but two methods of verification to login. Some applications are tied to an individual’s smartphone while others generate tokens directly on the device. Follow the steps below to turn on MFA for Zoom.
1. Log in to the Zoom Dashboard. In the navigation panel to the left, click Profile.
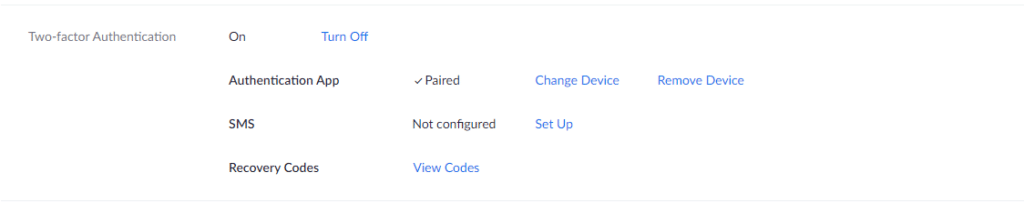
2. Scroll down to the “Two-factor Authentication” section and turn it on. Then, decide whether you want to pair an authentication app like Authy or if you want to receive SMS codes. Rocket IT recommends pairing an app to avoid potential security issues arising from SMS based MFA.
Despite the security recommendations above, the numerous issues surrounding Zoom have led users to search for safer alternatives like Microsoft Teams.
Microsoft Teams is gaining in popularity with more than 500,000 organizations adopting the platform as of December 2020. For businesses with an Office 365 Business or Enterprise plan, Teams is an included add-on that keeps everyone organized and operating on one central platform. The software serves as a hub for collaboration, making it easy for teammates to video chat, share files, sync calendars, and more.
Regarding security, Teams includes end-to-end encryption, multi-factor authentication, Rights Management Services support, at rest and in-transit encryption, and Secure Real-time Transport Protocol technology for audio and video data. In comparison, Zoom only offers optional end-to-end encryption, which has faced criticism in the past. Microsoft also provides detailed information about how it handles user data, unlike the vague language included in Zoom’s policies.
For more information on how Microsoft Teams can be deployed across your entire organization, feel free to contact Rocket IT at 770.441.2520 or fill out the contact form at the bottom of this page.
Related Posts
Subscribe to Rocket IT's Newsletter
Stay up to date on trending technology news and important updates.

Find out if Rocket IT is the right partner for your team
Claim a free consultation with a technology expert.