How to Prevent Zoombombing | Zoom Settings to Change
Meetings, classes, and networking events; a few of the common social gatherings that have felt the brutal impact inflicted by recent physical distancing ordinances.
And although such preemptive measures are necessary to fight the ongoing effects of COVID-19, taking such an approach just a decade ago would have resulted in the inevitable collapse of daily communication between friends, families, and colleagues. But alas, here we stand in the modern era; technology in hand, ready to overcome the communicative barriers that lie before us.
With that said, there are a number of software developers to thank for these rapid advances in telecommuting technologies. Major companies like Microsoft, Google, and Apple have all done their part in making it a smooth transition to remote work. But although these technology giants have played major roles over the years, current issues have placed a smaller company in the spotlight of consumer attention.
What is Zoom?
For those who have yet to hear of the web client known as Zoom, it’s a stand-alone software with web conferencing and webinar capabilities. As it currently stands, the service offers quite an impressive free plan; providing individuals with unlimited one-on-one calls, and the ability to host 100 participants in a single meeting for up to 40 minutes. Coupling this affordable price point alongside a simple user interface allowed the platform to be quickly adopted by businesses, educators, and students that were looking to remain engaged while working remotely.
But like many technologies that experience a quick upward trend in global popularity, it was only a matter of time before Zoom’s developers found themselves under the scrutiny of the public eye. Because Zoom’s original default settings made it easy to share meetings with the click of a link, the social platform became a huge target for those looking to cause some trouble. And while Zoom has drastically improved its backend security measures in recent months, it’s crucial that users of the program update their client settings to attain optimum security.
What is Zoombombing?
But before diving too deeply into those setting alterations, it’s important to first understand the cohesive role they play in protecting individuals and their data.
Known commonly as “Zoombombing”, mischievous individuals can take advantage of public meetings without security measures; dropping in to share explicit audio or imagery with an entire audience of people. In turn, while Zoom’s series of recent updates now give hosts the tools to adjust security measures on the fly, previous iterations did not; leaving organizers with no other option but to cut meetings short when faced with uninvited guests.
Yet, despite Zoombombing appearing as rather a childish and mild annoyance, this issue ultimately went on to serve as a reality check for Zoom’s security team. In the late days of March 2020, the cybersecurity expert known as Mitch@_g0dmode uncovered a vulnerability exploitable by Zoom’s previously lax security measures.
What Were the Previous Risks?
While the vulnerability has since been resolved, to get an idea of what it entailed, we first have to look at the Zoom chat feature. For those with a fluent understanding of Zoom’s interface, it’s likely that you’ve used the text chat feature that appears in every meeting. Previously, people were able to share hyperlinked web URLs and file paths to server-based documents through chat; allowing recipients to open said content with the single click of a button. Unfortunately, the Zoombombing conundrum allowed uninvited guests to join said meetings and share malicious links with groups of unsuspecting individuals. In turn, clicking a link posed the risk of data theft or the account being compromised.
Windows Password Stealing
Although these attacks previously posed a threat to all Zoom users, those using Windows devices were at an even greater risk. For Windows users, it was discovered that UNC paths could also be converted into clickable links. But what exactly is a UNC path? Simply put, UNC stands for Universal Naming Convention, a common tool for identifying servers, printers, computers, and other devices on a network. In turn, if a Zoombomber shares a UNC path that connects a user’s device to a remote server that they control, not only will Windows send the Zoombomber said user’s device name, it will also provide their login name and encrypted passwords. From there, it may take a skilled cybercriminal with access to third-party tools only a few minutes to crack simple password chains.
Windows Malware Injection
Alternatively, rather than simply sending a UNC path to steal credentials for later use, Zoombombers may have enabled malicious files to automatically download to devices that connect to the servers they control. In turn, this typically would prompt the user to approve the running of a downloaded application. But for those who are unsuspecting, it can be easy to carelessly click “OK” and accept the installation without thinking. In theory, not only would this provide the cybercriminal with the victim’s Windows login credentials, it would give the hacker an opportunity to remotely access the device and take full control.
How Has Zoom Resolved the Vulnerabilities?
While partial blame for these vulnerabilities can be placed on Microsoft, Zoom has done an excellent job pushing out updates on a weekly, if not daily, basis. For the time being, Zoom has completely removed the hyperlinking feature in its chat. In turn, users are forced to either copy and paste these links into their appropriate application for opening; or use another method of communication. And although not much word has been provided on when this feature will be reinstated, Zoom’s Founder and CEO, Eric Yuan, assured individuals in a recent blog that his team has completely resolved the UNC path link issue.
Additionally, the organization has taken some extra steps to cut down on the Zoombombing attacks that have plagued the platform for the last couple of months. In a recent email sent from Zoom’s support team, they outline some of the steps they’ve taken to protect those who continue to use the platform. While there are quite a few on the list, here are some notable examples.
Security Toolbar Icon for Hosts
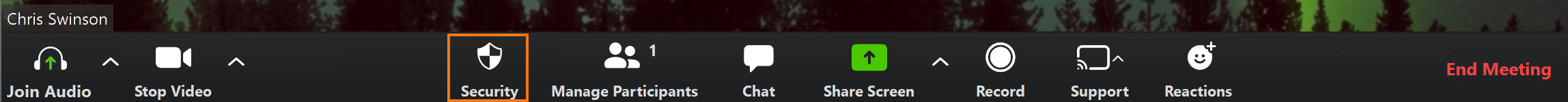
While it’s still best practice to enable security features before a meeting begins, Zoom’s recent update provides new security options directly in their meeting controls. As a result, hosts are no longer risk fumbling about during a call when attempting to adjust security settings. After starting a meeting, hosts can now click the security icon at the bottom of the client window to enable the meeting waiting room, lock the meeting, and alter the administrative rights of meeting attendees.
Meeting ID No Longer Displayed
When a Zoom host launches a call, the meeting is assigned a unique ID, containing 9 to 11 randomly generated digits. Previously, these IDs were publicly displayed for attendees to see. And although having these IDs publicly displayed made it easy to share meetings with colleagues, it also allowed Zoombombers to use what is now known as “war-dialing” programs. By using one of these third-party services, cybercriminals could rapidly cycle through possible Zoom meeting IDs and gain access to those without password protection. While it’s still important to password protect meetings, meeting IDs are now privately enclosed and can only be seen when clicking the information icon in the top-left corner of a live meeting.
File Transfers
As mentioned previously, clickable URLs have now been disabled in meetings. Taking this a step further, Zoom has also removed the ability to conduct third-party file transfers through meeting chat. That said, local file transfers have been introduced with a recent update, meaning colleagues can still share files if they’re on the same network.
How to Check Your Zoom Client Version
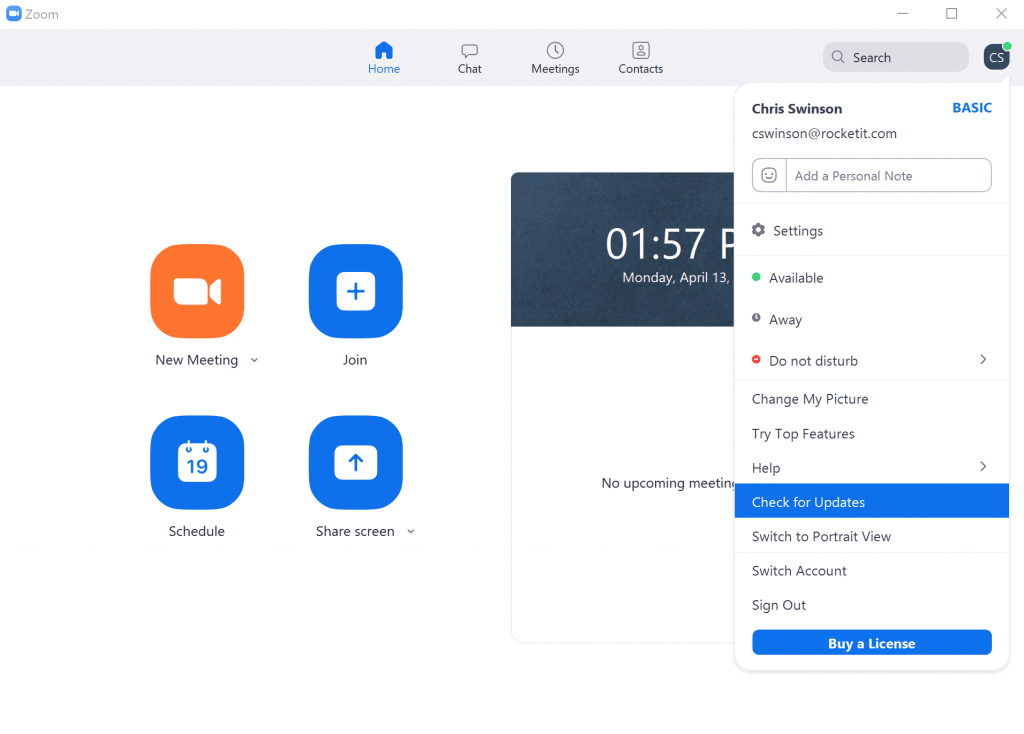
Keeping in mind that these updates only take effect if you have the latest client version installed, it’s important to ensure your Zoom application up-to-date. Currently, the Windows client is on version 4.6.10, and Rocket IT strongly suggests keeping the platform updated to mitigate security risks. To check your client version, open the application and click your account icon in the top-right corner of the window. From the menu, select “Check for updates”, and install the latest version if prompted.
Best Practices for Zoom Meeting Settings
While Zoom’s developers continue to update the back-end security measures of the application, there’s only so much they can do. In turn, the responsibility of securing meetings and the information discussed inside falls partly on the shoulders of those who host the calls. With that said, here’s a specially curated list of security settings that should be enabled to mitigate the risk of Zoombombing and other attacks.
Settings to Enable Before a Meeting
Rather than launching a meeting directly from the Zoom desktop client, consider scheduling a meeting via the Zoom web portal (zoom.us). In doing so, you’ll be given the opportunity to maintain far more control over the security of a meeting.
- Once logged into the web portal, navigate to “My Account” and select “Meetings” from the left navigation menu. Enter the topic, description, date, time, and duration as you normally would.
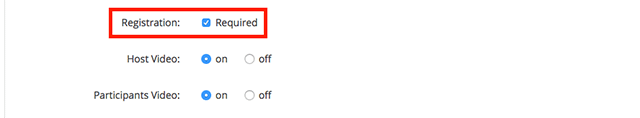
- For those individuals with a paid business, enterprise, or education plan, the next setting to enable is under the “Registration” setting. Scroll down and check the box next to “Required”. By enabling this feature, the invitation link sent out to guests will first direct participants to a registration page; where they are required to enter their name and email address before joining the call. This allows hosts to distinguish between attendees and will provide them with more control if something should go awry in the audience.
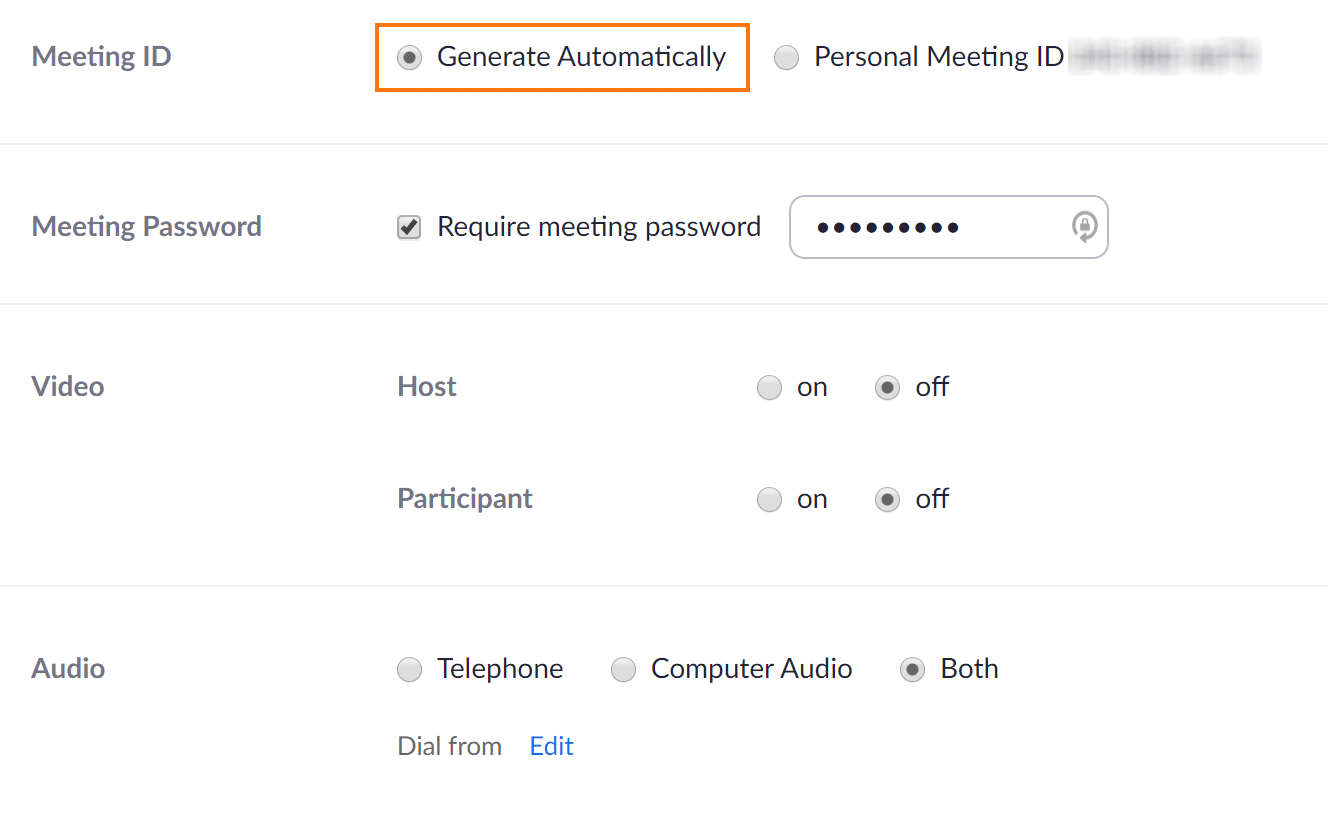
- Next, under the “Meeting ID” setting, ensure the tick-box next to “Generate Automatically” is selected. Taking this step will ensure a new and unique ID is assigned to each meeting you conduct; rather than your personal meeting ID being used repeatedly. If this setting is not enabled, Zoombombers that have successfully joined your calls in the past will have a far easier time doing the same in the future.
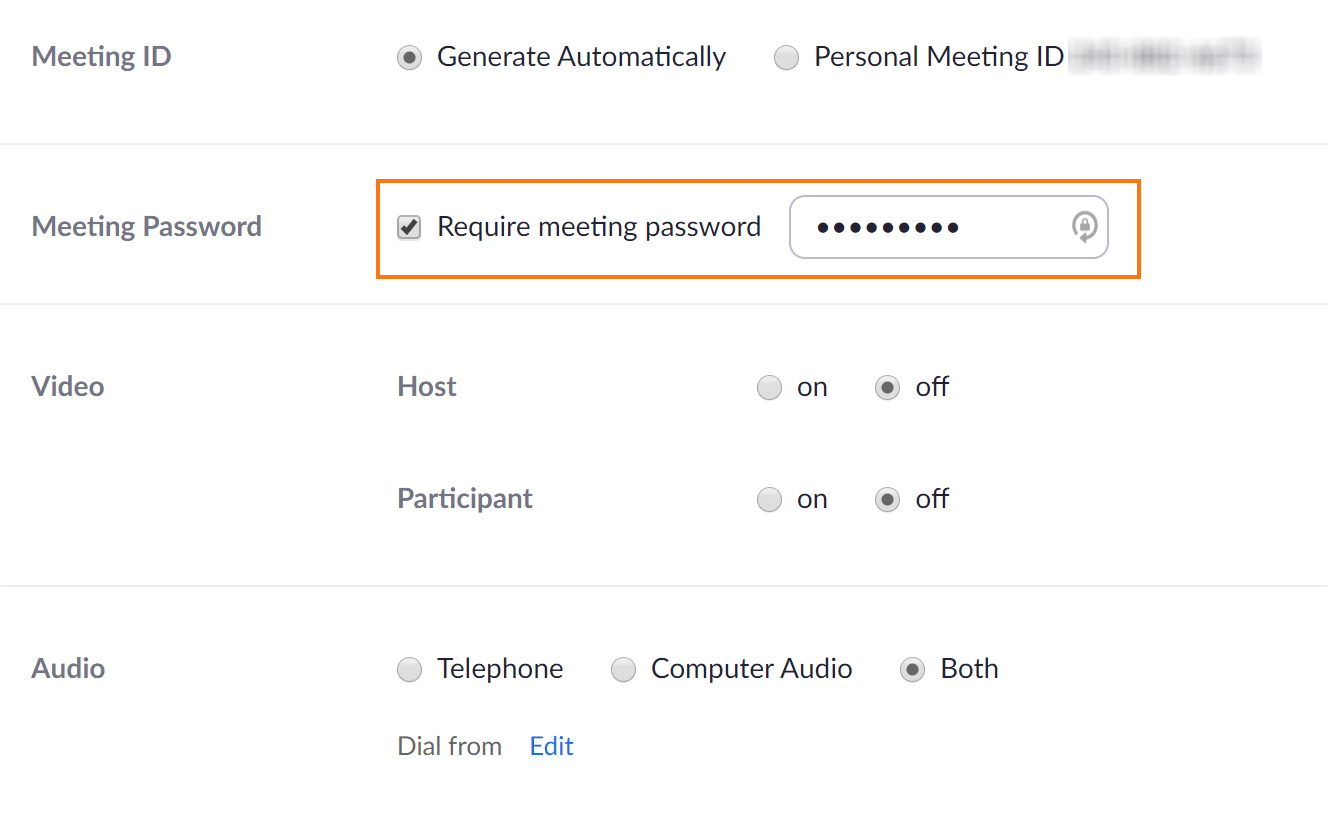
- For individuals that continue scrolling down the page, the option to “Require a meeting password” will be available. This setting is enabled by default, and Rocket IT strongly urges you to not uncheck this box. For steps on creating a strong password, check out this article on passphrases.
- The next setting pertains to the video stream of the host and the meeting participants. It is recommended to keep both of these settings in the off position and only turn them on once the meeting begins.
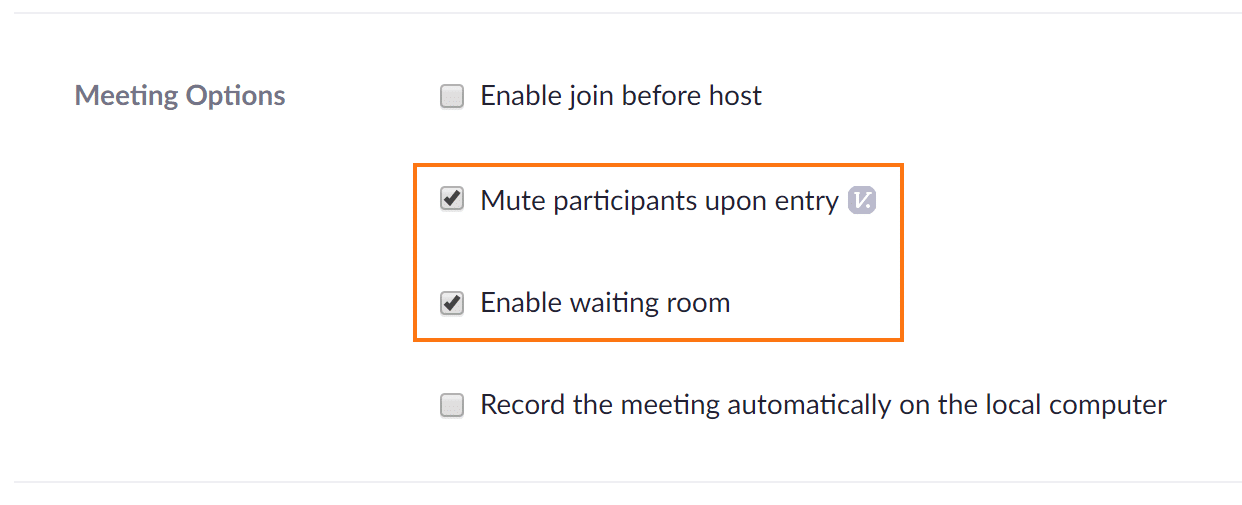
- The next three settings to enable lie slightly below, under the subcategory called “Meeting Options”. Here, make sure the box next to “Enable join before host” is left unchecked, while the checkboxes next to “Mute participants upon entry” and “Enable waiting room” remain enabled. Taking this step ensures three things. One, guests can not join before the host and hijack the meeting. Two, participants coming in and out of the meeting will not disrupt the flow of discussion. And three, hosts will be able to selectively move guests from the waiting room to the meeting; making sure to remove those individuals that are not recognized.
- Finally, for those with a paid business, enterprise, or education plan, make sure to designate an alternative host. This allows one host to share their screen and present, while the other manages participants and the chat.
Settings to Enable During a Meeting
While following the steps above proactively secures a meeting before it takes place, a few more security features should be considered once the meeting has begun.
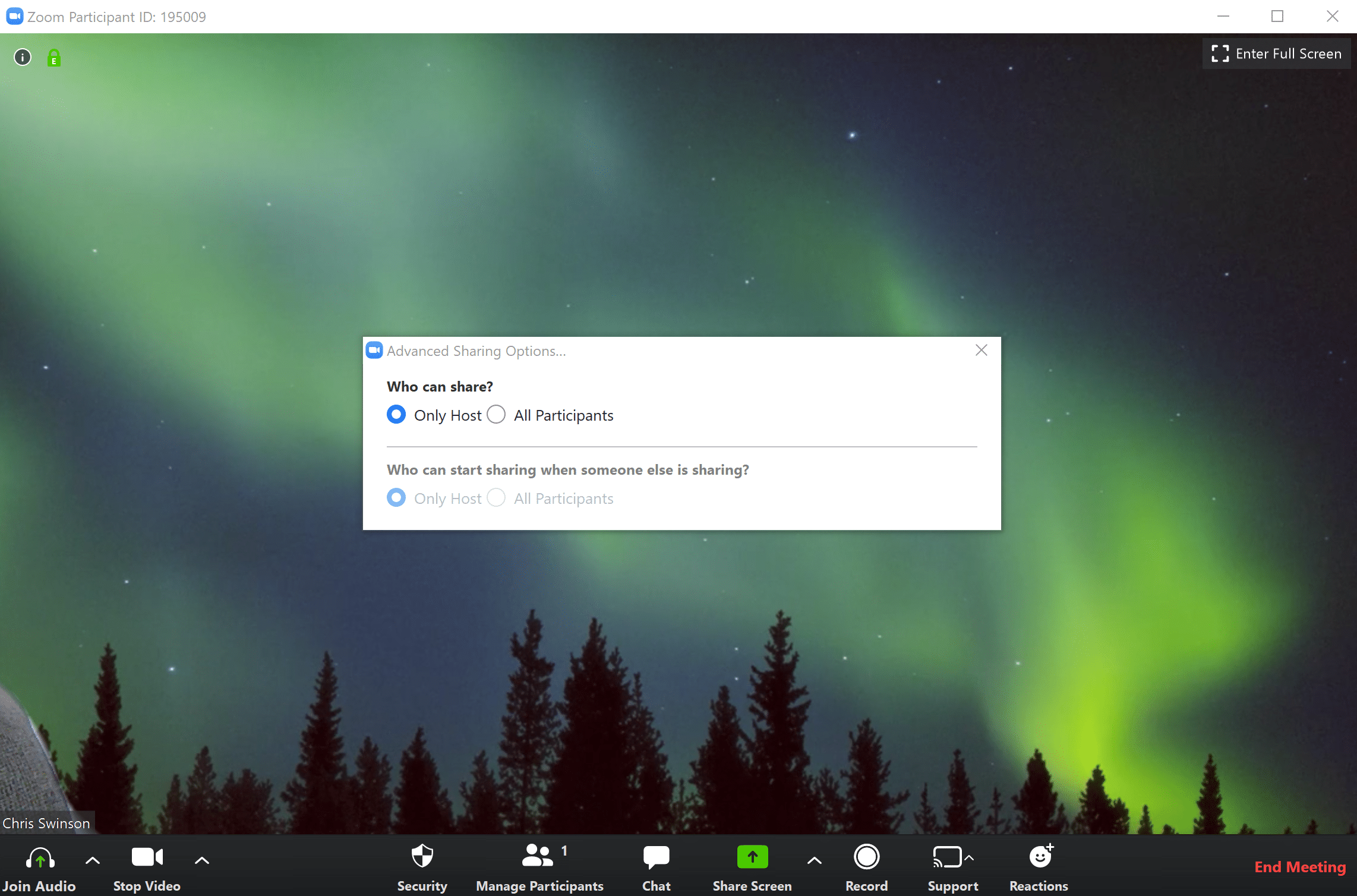
- After the scheduled meeting has begun, look at host controls at the bottom of the window click the arrow next to “Share Screen”. Make sure both “Who can share” and “Who can start sharing when someone else is sharing” are both set to “Only Host”. While this somewhat limits the option to collaborate, enabling these settings limits the chance of participant disruption.
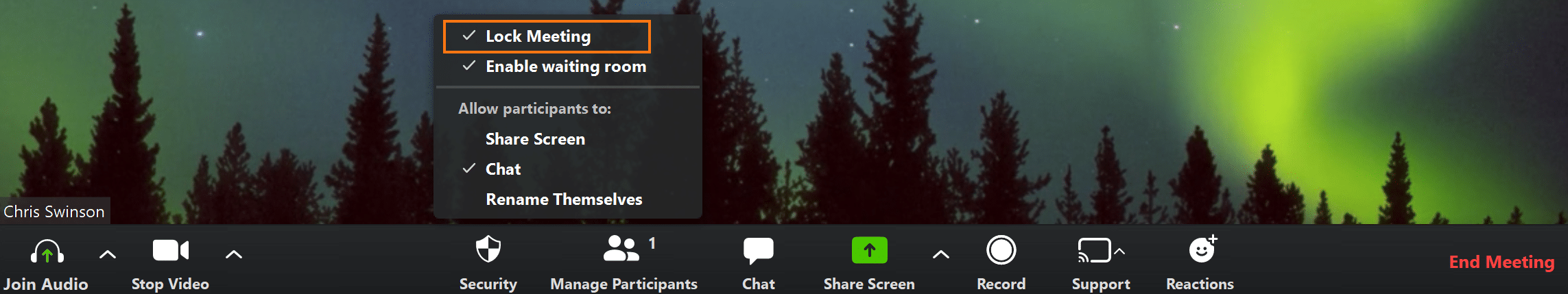
- As mentioned previously, Zoom’s recent update added a security icon to the bottom menu of the hosting screen during a call. After a call begins, Rocket IT recommends that hosts click the security icon and lock the meeting. This step should only be taken when the group is small and all members are accounted for.
- Finally, also under the security icon, hosts should uncheck the setting “Allow participants to rename themselves”. If registration was required beforehand, participants will be assigned the name given at that time. This will give hosts more control over the audience, and look for any troubling individuals they may have noticed in the past.
Final Verdict: Zoom is Safe to Use
As some states have now begun to prosecute Zoombombing as a crime, Zoom is hopeful that cybercriminals will think twice before entering the online platform. That said, Zoom remains an excellent outlet to maintain communication between family, friends, and colleagues. As it stands now, Zoom’s developers have found a balance between securing the privacy of users alongside the diverse telecommuting needs of the growing remote workforce. In turn, Zoom continues to offer end-to-end encryption; ensuring video, audio, screen sharing and chat are protected whilst being exchanged between individuals.
By following the steps above, individuals can elevate the back-end security measures that Zoom has published, and make sure the platform remains a viable source to conduct business. For more settings to improve your Zoom experience, Rocket IT invites you to visit rocketit.com/zoom-easter-eggs/ to read about lesser-known features hidden deep within the app.
Related Posts
Subscribe to Rocket IT's Newsletter
Stay up to date on trending technology news and important updates.

Find out if Rocket IT is the right partner for your team
Claim a free consultation with a technology expert.