Tax season is coming soon, and with it comes W-2 phishing season (and not the bass fishing many in Georgia love). As HR and Accounting departments are preparing tax documents for their employees, cybercriminals are targeting that information using social engineering tactics in phishing emails.
(Want to learn more about ransomware and how to keep your organization safe? Get our free Security in the Age of Ransomware webinar on demand here.)
The phishers take advantage of the pressure during this time and send urgent requests to end-users requesting confidential information, typically while posing as a high-ranking executive (They’re not who you think they are).
This method is known as “spoofing” and is a common spearphishing tactic. Spearphishing is a specific form of phishing that uses knowledge of companies, their internal hierarchy, email addresses, and individuals to trick victims into believing the attack is coming from a trusted source. That means these emails can appear to come directly from a legitimate email address and include the same email signature that individual uses.
Phishing emails can range from glaringly obvious phishing attempts (think from sysadmin_rocketit@gmail.com) to incredibly sophisticated social engineering emails that are much harder to spot using the untrained eye.
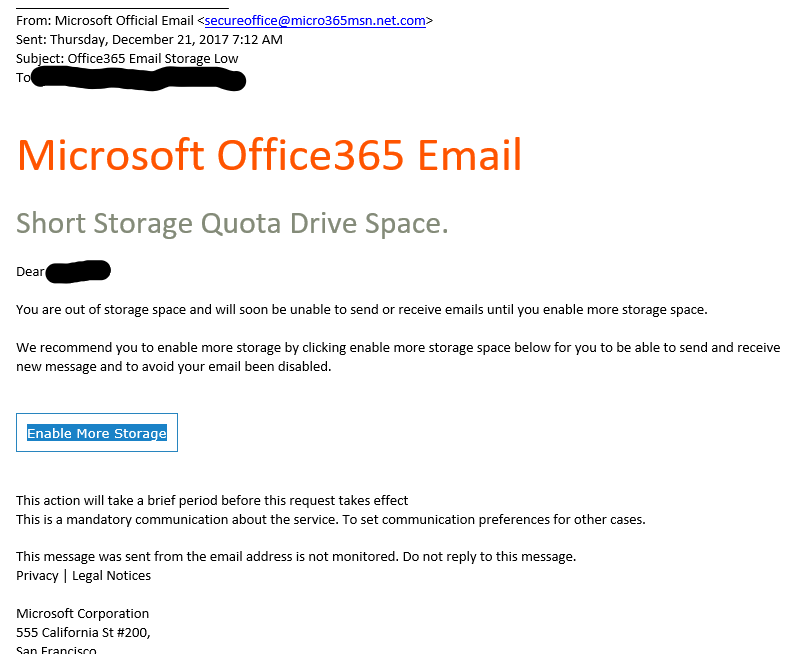
Consider this phishing email example below.
Taking a look at the email address, many untrained end-users wouldn’t spot the unusual domain. It appears to be from an official source, and the message itself looks pretty official.
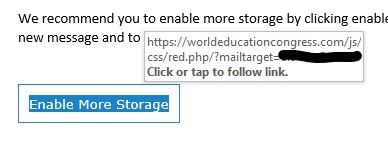
By hovering over the link (without clicking on it), you can see a preview of the URL to which it actually leads.
This link takes you to a different location than the email leads you to believe it will, and it’s definitely malicious.
You and your employees can be trained to spot phishing emails like these, no matter what their call to action to you is. For other emails, like spoofed ones from internal executives without an actual link, but calling for a wire or data transfer, can be a little more difficult.
Email Phishing Prevention
So how else can you prevent your organization from falling victim this W-2 phishing season?
Put processes in place that check the transfer of funds and information before they occur. If an executive makes a request via email for confidential tax information, make sure your employees have an extra confirmation step in place either in person or via phone to confirm this request with that executive. You can also create a step where employees must confirm with their manager or another executive what information can be sent before responding.
If you respond directly to a potential phishing email to confirm, that response will go back to the phishers. Do not respond directly to that email for confirmation rather than picking up the phone; if you do, you could still end up being the victim, despite your processes.
If an executive or other employee’s login information has been compromised (likely by another phishing email), their account could be compromised in general, which is why we recommend requiring a method other than email (in-person, phone, or text) for a confirmation.
Need help with setting up the right phishing prevention training and processes for your organization? Contact us. We’d love to help.