Upsurge in Phishing Activities: Don’t Take the Bait!
We’ve recently seen an increase in sophisticated phishing e-mails that could have resulted in significant financial loss. To help you detect the attempt before taking the bait, we’ve pulled a great article from our archives and updated it for your benefit.
The Internet is full of friendly people. There are Nigerian princes who want to give us a piece of their oil fortunes, in exchange for some basic bank account information, or long-lost relatives coming out of the woodwork to wire us multi-million dollar inheritances. To say nothing of the generosity of strangers: just the other day, a kindly foreign national wanted to split his investment proceeds with us, even though we had never met him.
Chances are, your spam folder is full of these laughable “once-in-a-lifetime” opportunities. They’re called “phishing” attacks in IT circles. The term refers to any attempt to acquire information such as usernames, passwords and credit card or bank information from the unsuspecting public through illegitimate emails, websites or other forms of communication.
While wayward Nigerian royals and uncles you’ve never heard of may sound like the Three Stooges attempting cybercrime, other phishing attacks aren’t as easy to detect and bear more of a resemblance to a criminal mastermind like Professor Moriarty than to Larry, Curly and Moe.
Advanced phishing attacks are highly organized, highly targeted and highly dangerous. They’re also on the rise. According to a recent study by Internet security firm IID, phishing attempts for Q1 2015 were up 8% when compared to Q4 2014; 2014 having been declared in their Q4 2014 report “The Year of the Breach.” The expert criminal minds behind advanced phishing attacks often try to bait an email recipient into “biting,” or clicking, on a link within an email. That link takes the user to a fake website that looks similar or identical to its legitimate counterpart. There, a user is prompted to enter a username, password or other piece of personal data, which is then sent to the malicious third party—who laughs all the way to (your) bank.
To protect yourself from these fake links and websites, it’s important to understand the two main parts of a link: what you can see and what you can’t.
Most email messages and all websites use a language called HTML in order to tell your email application or web browser what to display and how to classify the different elements of a message or a page. One of the fundamental components of both HTML email messages and web pages is the link, which is also referred to as a URL, or Uniform Resource Locator.
A link in HTML looks like this:
In the example above, the only portion of this link visible to you is “Visit us at www.rocketit.com!”While clicking on this link would take you to the Rocket IT website, making the following changes to the link would result in sending you to an entirely different location:
The link above would also appear as “Visit us at www.rocketit.com” in the body of the email message or text of the web page. It’s easy to think that a link like this would send you to our actual website,www.rocketit.com. However, the link would actually send you to www.stealmyidentity.com, a site that could easily be malicious.
The easiest way to verify a link’s legitimacy is to hover your mouse cursor over the link. When you do this in your email client, a pop-up box appears that shows the destination URL. If you’re using a web browser, that URL should appear in the status bar at the bottom of the browser window.
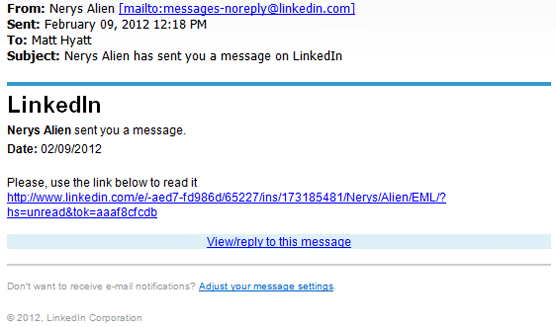
For example, the email message below looks similar to the notification that professional networking website LinkedIn sends you when you’ve received a new message. But when you hover the mouse cursor over this link, the pop-up box appears—showing you that the link leads to an entirely different place.
If your email client or browser doesn’t show the link destination, there’s an alternate way to ensure that a link is safe by copying and pasting the link URL from the source message. Start by right-clicking on the link and selecting “Copy Hyperlink” from the pop-up box. If you’re copying and pasting from a browser, this option may be listed as “Copy Shortcut” or “Copy Link Location.”
Be careful you don’t accidentally click “Open Hyperlink” or “Select Hyperlink.” Both options will send you to the link’s destination.
Then, open a safe application such as Notepad or Microsoft Word. Right-click and select “Paste” from the pop-up menu to copy the link to a blank document. You can also do this by pressing the “CTRL” key and the “V” key at the same time.
If the link shows any other destination than the one you expected, do not visit the link.
It is important to note that websites often use variations of their domain which are completely legitimate. For example, amazon.com might use the “sub-domain” wireless.amazon.com for their cell phone store. The end of the domain (amazon.com) is what is important.
But if the link contains a fundamental variation of the standard domain name, something like www.amazon12.com, it may be a fake form of the URL and could be designed to steal your Amazon username and password.
In addition to destination URLs that do not match the text of the link, there are two other dead giveaways that a link is malicious. If the link connects to a foreign domain, such as “.ru” or “.cn”, there is a good chance that the link is not safe. (Note that the link in the first example connects to the domain “golestangis.ir”, which is a domain for the country of Iran.) Many organized phishing scams originate from Russia (domain “.ru”) and China (domain “.cn”).
If a link includes an IP address, such as http://15.8.145.152, then it is almost certainly not safe. As a general rule, legitimate sites do not use IP addresses in the link text.
Always remain vigilant. Many different forms of phishing attempts exist-and these messages are designed to be compelling and indistinguishable from the sites they purport to represent. If you’re unsure of a communication’s source, it’s never impolite to directly contact the company or person being represented to verify a link’s legitimacy. You’ll be glad you did.
Matt Hyatt is the Founder and CEO of Rocket IT, the IT department for all kinds of organizations around Gwinnett. His award-winning firm provides both the strategy and support needed to help businesses thrive.
Matt currently serves on the Executive Board of the Gwinnett County Chamber of Commerce as the Vice Chair of Entrepreneurship & Small Business, is an active supporter of Gwinnett County Public Schools, and is a member of several peer groups (like Entrepreneurs’ Organization) in addition to cofounding two of his own. In 2014, Matt was awarded the Pinnacle Small Business Person of the Year.
Outside of work, Matt enjoys spending time with his wife, Maureen, and their two teenage children pursuing their shared passions for photography, travel, and food. He also regularly runs with a team in ultra-long distance relay races.

Related Posts
Subscribe to Rocket IT's Newsletter
Stay up to date on trending technology news and important updates.

Find out if Rocket IT is the right partner for your team
Claim a free consultation with a technology expert.











