
The 2020 Twitter Bitcoin Scam & the Future of Social Engineering

Elon Musk, Bill Gates, Apple, Uber, Jeff Bezos, Barack Obama, and Kanye West: what do they all have in common? Aside from being notable businesses and individuals to audiences across the globe, each of these entities fell victim to a cyber attack that hit Twitter on July 15, 2020.
On that day, Tweets from the aforementioned accounts and 38 other verified users were posted, offering millions of followers what appeared to be the investment of a lifetime. In the fraudulent tweets, individuals were told that if they donated Bitcoin to a COVID-19 relief fund within the next 30 minutes, they’d receive double the value they contributed.
How the Scam Occurred
Before Twitter could act and inform its user-base of the misleading Tweets, hundreds of individuals collectively submitted around $180,000 to what was ultimately an unidentifiable cryptocurrency account controlled by one anonymous individual. Once the breach was inevitably discovered, Twitter authorities locked all verified accounts; resulting in many notable individuals being unable to reach out on the social media platform for a few hours while an initial investigation occurred. Not knowing how far the attack had spread and what the infiltrators were after, Twitter administrators took further action by locking down any account that had requested a password change within the last 30 days. And finally, as a last precautionary measure, Twitter enforced emergency security policies across the company, revoking employee access to many internal tools as the attack ensured.
But how exactly did this attack occur, and what can we learn from it? In a recent blog post from Twitter, the ongoing investigation has shown evidence that some Twitter employees with administrative access to high level tools and important internal systems were the target of a social engineering scam.
Unlike many standard phishing scams that take a single email to acquire information, social engineering scams tend to be more elaborate; taking criminals weeks or months to complete. For a successful social engineering attack to occur, cybercriminals carefully observe individuals behavior before engaging through an online platform; such as email or social media. Once they’ve gathered some background information, the scammer will initiate some form of communication in hopes that it will develop into a series of discussions. From these conversations, the hacker slowly builds a false sense of trust with the victim, only to later use that trust to manipulate the individual into compromising important information that they’d typically not provide to a stranger. Once the hacker has gotten the information they need, they’ll quickly bring the conversation to a natural end in hopes of not arousing suspicion.
Generally speaking, the communication of these attacks usually take place via email, but the New York Times discovered that the social engineering attack that recently hit Twitter had a high likelihood of developing inside the organization’s internal Slack channel; an app commonly used by web developers. That said, Twitter has yet to announce how the culprit may have successfully infiltrated their private communication network, nor have they mentioned what information was relayed.
Results of the Attack
As you can imagine, no firewall or antivirus measures can stop a social engineering attack from occurring. Instead, this is a form of user error that requires training and self-awareness to prevent. While a baseline phishing security test can help organizations pinpoint those employees that pose a risk, Rocket IT strongly recommends that company-wide security awareness training occurs on a regular basis to ensure team members are prepared to handle the ever-changing nature of social engineering attacks. But Rocket IT isn’t the only organization pushing this sentiment. In a recent blog posted by Twitter, executives of the business stated that it would be launching new security training policies and phishing testing would be a requirement for all employees throughout the remainder of the year and beyond.
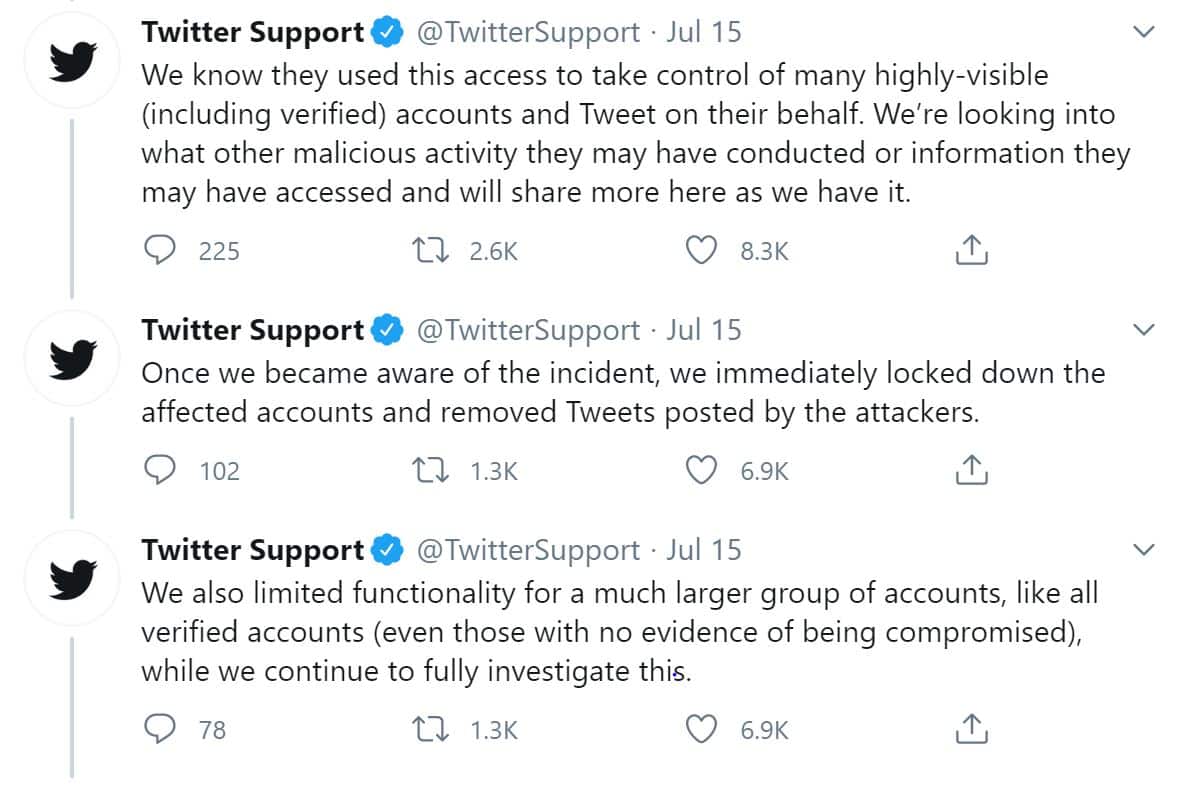
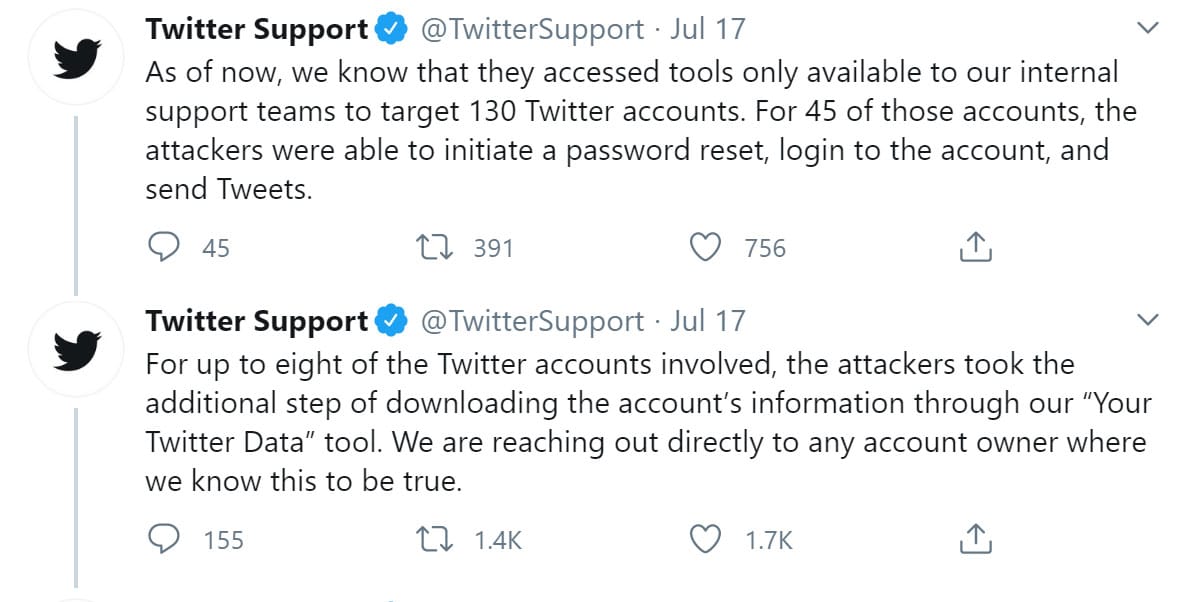
As you might expect, failure to successfully identify and thwart a social engineering attack can have devastating effects. As for Twitter’s recent breach, a total of 130 accounts were compromised. Of those accounts, 45 had password resets initiated; allowing the attacker to login to these accounts and send Tweets. While Twitter has continued to be forthcoming with information as the investigation continues, the organization has yet to reveal what other data may have been stolen; including personal, direct messages between powerful individuals. That said, the evidence that has been provided shows that eight accounts had a summary of their Twitter account details and messaging activity downloaded; an activity that is commonly conducted when hackers are looking to sell user information on the black market. Additionally, it has been confirmed that attackers were able to view the personal phone numbers and email addresses of those accounts accessed.
Pushing those negative findings to the side, Twitter has made it a point to confirm that attackers were unable to view previous account passwords, and this was not a wide-scale attack. While twitter has already begun to allow individuals to regain access to accounts, if you’re still waiting, understand that Twitter is looking to ensure it’s giving access to the rightful owner. As a precaution, once you regain access to your account Rocket IT strongly suggests implementing two factor authentication for your account. For more information on what 2FA entails, check out this blog that goes into full detail.
How to Spot Social Engineering
Nevertheless, social engineering is not a method of attack that will cease overnight, and the recent attack that hit Twitter should be viewed as a warning sign of what may come without proactive security measures in place. While formal security training is necessary to achieve heightened protection, here are some tips on how you can spot a social engineering attempt in the future.
Question the source
Even if you think you know the person requesting an action, don’t be too quick to hand over information. If it’s an internal email, make sure the email address isn’t getting spoofed by a hacker to appear as though it’s coming directly from an authoritative figure. Should you be unsure, don’t be afraid to pick up the phone and call the person in question. Alternatively, if you’re on social media and notice a celebrity or other individual promoting a link, research that link before clicking. If it’s claiming to be for a philanthropic cause, conduct a factcheck to ensure legitimacy. Finally, if you’re still feeling uncertain, reach out to an official representative with that website to determine if the campaign is real or fake.
Look at the details
Is it a strange URL? Is the image quality grainy? Do the logos seem slightly off? Are there typos? If it’s an email from someone you aren’t particularly familiar with, do they know slightly too much about you? These are the questions you need to be asking yourself when viewing content on the web.
Is there a sense of urgency
Social engineering is more effective under times of urgency and pressure. Hackers don’t want victims to think hard, but rather act quickly. Because of this, it’s important to slow down and think logically before acting upon a request from a suspicious source. Don’t let fear or excitement get the best of you.
Is the offer too good to be true
Similar to the attacks that hit Twitter, free giveaways are a common ploy in social engineering schemes. Before hastily providing your information or money, think about why someone would be providing you with this offer. As the saying goes; if the offer sounds too good to be true, it probably is.
To learn more about the tell-tale signs of a social engineering scam and the security training measures used to protect your team against them, feel free to give Rocket IT a call at 770-441-2520, or contact our team using the form below.
