What Is Spear Phishing? | Definition & Prevention

The modern cybercriminal’s toolbelt has grown quite a bit in recent years. But despite all the new technology these hackers have access to, it’s the simplest of tools that many businesses find the most difficult to defend against.
Spear phishing is nearly undetectable by modern antivirus software and breaches from these attacks can result in significant monetary and reputational loss.
What Is Spear Phishing?
At its core, spear phishing is a lot like your general phishing attack. It’s a confidence scam used to steal information or money from unsuspecting businesses. But that’s where the similarities end.
Rather than sending messages to thousands of email addresses at once, spear phishing requires cybercriminals to determine the data they’re after and who has access to it. Once they have their target in mind, the cybercriminal carefully researches the individual to impersonate a person or company they regularly communicate with.
As a result, successful spear phishing campaigns can often yield larger payouts than their standard phishing counterparts, such as business secrets or confidential information.
Knowing what’s potentially on the table, spear phishing has increased by 127 percent in just under a year, posing a huge risk to nearly every organization.
How It’s Done
But before learning how to counter this massive uptick in spear phishing attacks, it helps to know how one develops.
- Step One – Identify
- Before any scamming can occur, a cybercriminal needs a target. For many scammers, the low hanging fruit is often the most obvious choice. Using an automated script, a cybercriminal will crawl LinkedIn profiles, company staff pages, and search engine results for public email addresses.
- Step Two – Research
- With a list of email addresses in hand, it’s time to research a target. Once selected, the scammer discovers who the target regularly communicates with and builds an email template to match the sender they’ll impersonate.
- Step Three – Purchase a Domain
- With their target selected and message ready, this next step is crucial. Email providers, like Google and Microsoft, have strict spam filters to protect their users from junk mail. To get around this, cybercriminals purchase domains with good reputation scores from a reputable hosting site, like GoDaddy or HostGator. Using the free email server that comes with the domain, the scammer will then trick Gmail or Outlook into thinking the email is from a trusted sender.
- Step Four – Collect the Bounty
- If the email is timed correctly, it’s likely the target will respond quickly. From there, it’s up to the cybercriminal to continue the conversation and build a foundation of credibility. Once that sense of trust is established, the target is more likely to complete the scammer’s request.
Real World Example
To get an idea of how spear phishing can play out in the real world, let’s look at how a Rocket IT customer successfully thwarted an attack.
In early 2023, a firm out of metro Atlanta purchased another business to expand its operations. To announce this purchase, the company published a public press release on their website. Cybercriminals saw this press release and researched the firm’s executives.
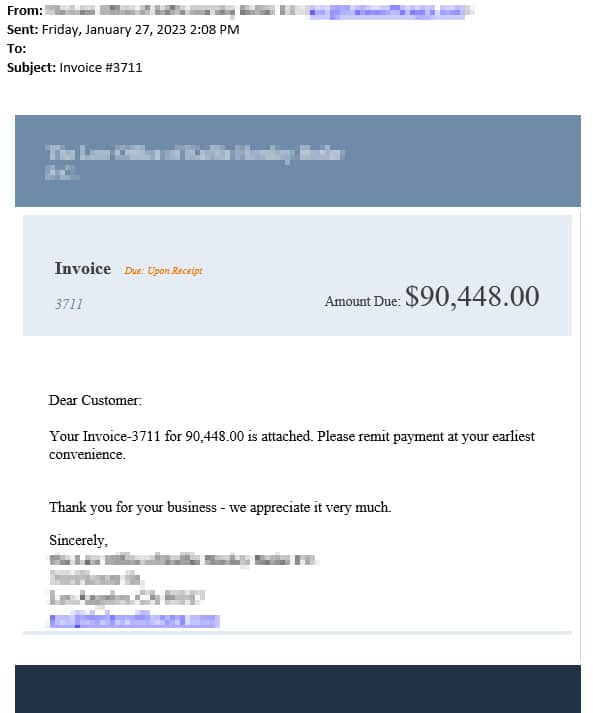
After discovering one of the executive’s email addresses, the cybercriminals purchased a reputable domain, fabricated a fake law firm, and sent a fraudulent invoice for $90,000.
While cybercriminals knew the target was anticipating an invoice to finalize the merger, they didn’t expect the executive to vigilantly report the false invoice.
How To Prevent Spear Phishing Attacks
Defending against spear phishing attacks requires a multi-layer approach and with just a few changes you can greatly mitigate the chance of a breach.
Remove Public Email Addresses
Many companies have a page on their website to highlight executives and other staff members. There, you can often find each individuals’ email address. While this makes it easier for customers to reach out, it also makes a cybercriminals job extremely easy.
Instead of publicly listing email addresses, consider embedding a contact form on the site.
Check For Exposed Email Addresses
While you might be taking the right steps to keep your email secure, a third-party data breach can leave you exposed. When a service you use for business is breached, the first thing hackers obtain is a huge dataset of email addresses. Cybercriminals will them pose as the brand they breached to conduct spear phishing campaigns.
To check if your email address has been exposed through a breach, check out this website.
Contact the Source
If you receive an email requesting sensitive information, a wire transfer, or large payment, be cautious responding to the message. Instead of replying via email, pick up the phone and call the individual you believe is making the request.
While calling does add an extra step to the process, this level of cautiousness can save you thousands of dollars.
Train Your Team
Although you can deploy modern spam filters and firewalls to keep spear phishing campaigns at bay, it’s only a matter of time before a malicious email makes it through.
Through security awareness training and phishing testing software, Rocket IT helps teams understand signs of security threats, identify individuals most vulnerable to attack, and mitigate the risk of your organization being breached.

Related Posts
Subscribe to Rocket IT's Newsletter
Stay up to date on trending technology news and important updates.

Find out if Rocket IT is the right partner for your team
Claim a free consultation with a technology expert.










