Case Story | Financial Spear Phishing
The number of hacking communities using spear phishing tactics to steal revenue from small-businesses is growing. In 2019, 88% of organizations worldwide admitted to having experienced a spear phishing attempt of some kind. While many of these businesses were able to properly defend their assets, the success rate in blocking a spear phishing attack relies almost entirely on the skills of employees and individuals in financial roles. Noting that the social engineering behind these attacks is quickly becoming more complex, it’s critical that every team member receive the training needed to be a cybersecurity expert.
You’re a Family-Owned Construction Company
For a moment, step into the shoes of one of Georgia’s oldest, family-owned construction companies. Over the course of 95 years, your business has upheld a mission to deliver high quality work in a timely manner while remaining on budget. Because your team works on a wide array of projects across the state, hundreds of calls and emails come in each day, requesting payment for the resources used to complete construction projects.
Your Industry Is Full of Risks
While a vast majority of these incoming financial requests are legitimate, a recent study landed on your desk, revealing that spear phishing scams involving payment and invoice fraud increased by 112% in 2020. While your company already works with Rocket IT to deploy harmless phishing emails to test employees, you know the construction industry remains one of the top three industries at risk for “phish-prone” individuals.
Over the Next Few Days…
A few days after hearing this news, one employee in charge of account receivable payments receives a suspicious email appearing to come from the address of a vendor. In the email, the person claiming to be a vendor urgently requests that all future payments be directed to a new bank account.
In addition to this new information, the potentially fraudulent email requests that your accounts payable person send $60,000 to this new account to cover the cost of a previous project. As with any financial request, a seemingly normal invoice is attached to the email.
Understanding that accidents on and off the construction site can be avoided with preemptive measures, you’ve already ensured your finance team participates in regular training seminars with Rocket IT to ensure they’re up to date on current cybersecurity threats. By coupling this training alongside regular phishing testing, these individuals have the knowledge and foresight required to prevent a phishing attack from costing your business thousands in lost revenue and productivity downtime.
Your Team Follows Procedures
Recalling the time spent in training and the strict processes the organization has in place, your accounts payable person finds the vendor’s phone number on file and makes a call to verify the changes to previous payment instructions. Slightly overwhelmed, the vendor confirms that the change is correct and rushes your accounts payable person off the phone.
As with any call involving the transfer of money, your employee follows standard operational procedures and makes a note of the call’s time, date, the name of the representative they spoke to, and includes that they explicitly asked if this change was valid. After this step is complete, the team member then proceeds to wire $60,000 to the vendor’s new bank account.
A few weeks later, the vendor calls to say that they never received their $60,000 payment. As it turns out, a scammer had researched your company, found a vendor relationship, and exploited that relationship through a spear phishing campaign.
Thanks to your standardized record keeping, your accounts payable person quickly proceeds to provide documentation and phone records, with information detailing the call with the vendor’s point of contact that confirmed the change in banking information.
After some deliberation, the vendor agrees to take a $60,000 loss for an unpaid invoice and your business is not liable for the mistake.
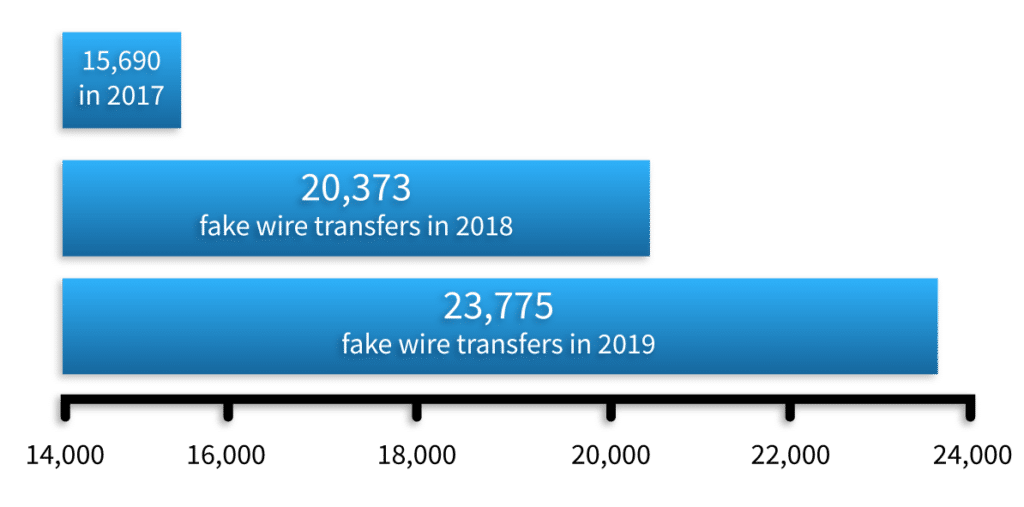
The Playing Field Is Changing
For high-target industries and individuals in financial positions, cybersecurity training and phishing testing is not something that can be done on one occasion and forgotten about. Because the social engineering behind spear phishing campaigns changes with current events, training and testing must occur on a regular basis to mitigate the risks of both new and seasonal attacks.
“Between the months of January and June of 2020, the number of phishing attacks witnessed was more than what was seen throughout all of 2019,” said Rocket IT Service Manager, Bria Soyele.
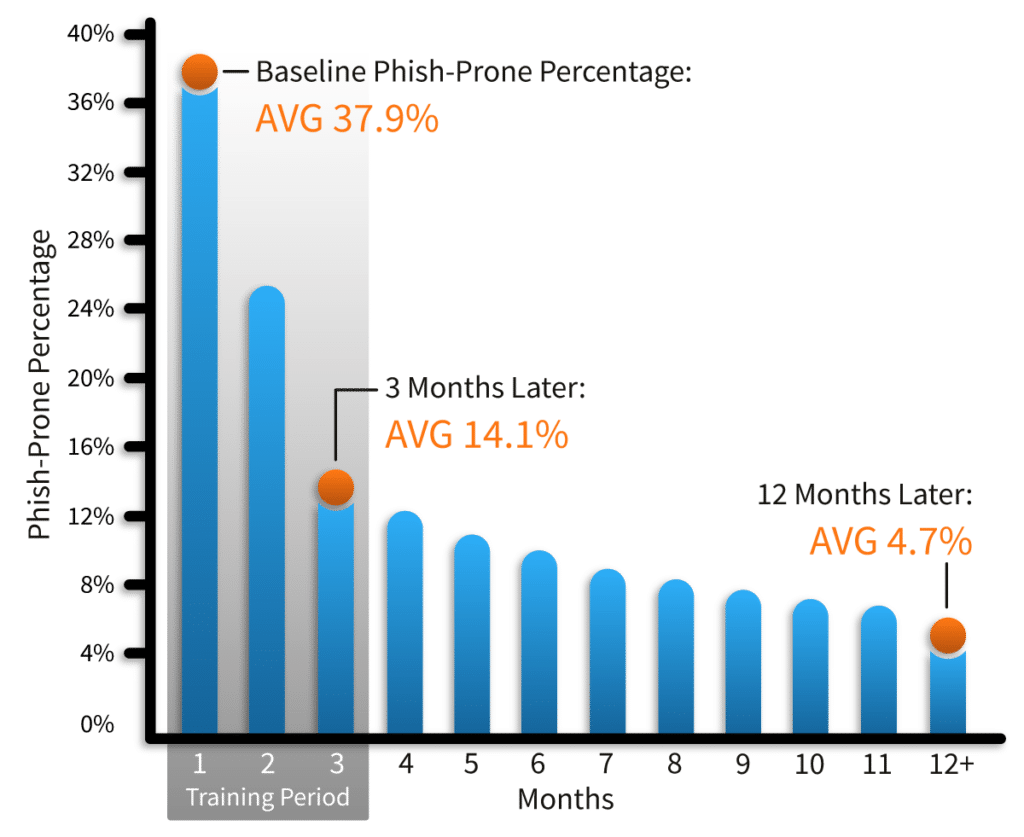
Using untrained individuals as a baseline measurement, the average employee has a 37.9% chance of falling for a phishing scam that could potentially impact their employer’s success. After three months of testing and training, this statistic quickly drops to 14.1%. And for those businesses that continue to participate in phishing testing for an entire year, trained employees only have a 4.7% chance of succumbing to a phishing email.
So, with the number of complex phishing campaigns increasing and untrained individuals still posing a risk to the success of many businesses, what is your organization doing to ensure it doesn’t become part of the statistic?
Related Posts
Subscribe to Rocket IT's Newsletter
Stay up to date on trending technology news and important updates.

Find out if Rocket IT is the right partner for your team
Claim a free consultation with a technology expert.













