How to Tell If An Email Address Is Valid

With most business transactions taking place at least in part over email, phishers have gotten very sophisticated at mimicking typical emails users receive and tricking innocent end-users into clicking on malicious links or opening corrupted files.
So how do you tell if the email you just received is valid… Or a Trojan horse in disguise?
You’ve received an email, and something about it just seems fishy, but you’re not sure. And you don’t want to miss out on an important business opportunity.
The first thing you can do is check the email address of the sender. If the email says it’s from LinkedIn Customer Support, but the return address says bclyde@linkin.com (notice the missed ED), then it’s a safe bet you should send that email straight to your junk folder. Scammers like to use email addresses that appear similar to the original domain they’re impersonating, and they’re counting on you to skim and look over those details.
Next, check the validity of all the URLs they’ve included in the email WITHOUT clicking on them. If you hover your mouse over a URL, a preview link will appear above it. Does this link lead to a different site than the one they’ve presented in their text? Check each link individually since some hackers will use legitimate links mixed in with their phishing URLs to lure you into a false sense of security.
Email Attachments
Is there an attachment included in the email? Without opening it, check the following: were you expecting this attachment? Is it from a trusted sender? Is it in the usual format you expect from that sender? It’s very common for phishers to spoof an actual email address from a trusted person (even within your own organization) and make it appear as if the email is really coming from that person, as well as enable the phisher to receive replies to that email as if they had access to the account they spoofed.
Best practices for email attachments are to follow up with the sender in a new email (okay), over the phone (better), or in-person (best) to make sure the attachment is really from them. You should ideally never open an unexpected email attachment. If you absolutely must open an attachment against all advice (again, please don’t!), be sure that Macros are automatically disabled through all of your programs (Adobe Acrobat, Word, Excel, etc.).
If an attachment prompts you to connect to outside links or run Macros, DO NOT GIVE IT PERMISSION TO DO SO. Enabling this in a file will allow it to connect to an outside server and run processes on your computer without your permission.
Email Headers
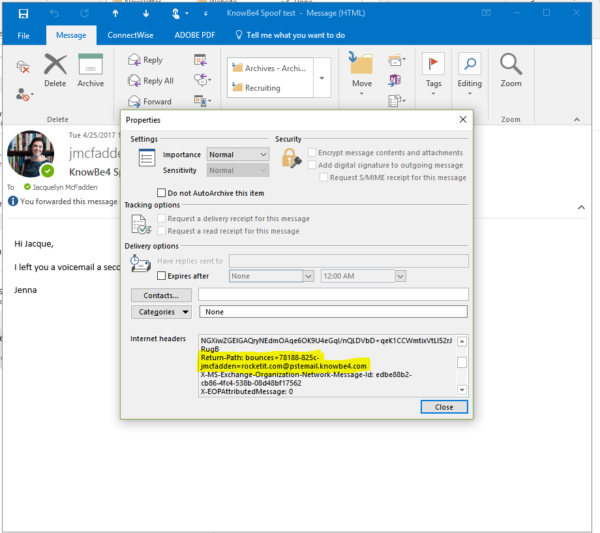
If you want to really get into the technical nitty-gritty, you can check the header of an email to see if the message is being sent from someone on the same domain server as the sender. If a hacker is spoofing the email address, a clue could be hidden in the header information.
To check the header in Outlook 2016, 2013, or 2010, open the individual message in its own window and click on the File tab. From there, select Properties in the Info tab. The header information will appear in the Internet Headers box. Here’s how to open the same in Gmail.
The information in your header box is ordered by the most recent action and later. So the information at the top will be from when you received it. To see where the email originated from, you’ll have to look at the earlier actions.
In the header information, scroll through to find Return-Path. This section should reveal the real reply email address of the sender. If an email is being spoofed, this address will be different from the original sender.
Another clue to watch out for in your information can be found in the sending server’s domain name. If an email hops around multiple servers (which is common with legitimate emails as well), look at each Received: from function. The further into your header information you go, the more likely you are to catch the real domain address of the original sender. Seeing one email hop that matches, especially in the beginning, is not a good indicator that the email is valid, as spoofers can trick that function later on. You need to make sure each server hop resolves the sending server back to the purported sender’s domain.
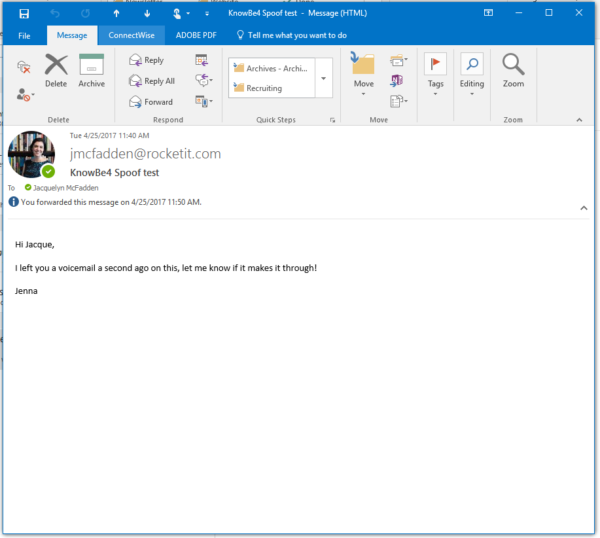
For example, the email below appears to be coming from our Marketing Specialist, but when we go into the header, we can see that the email is really from our friends over at KnowBe4.
While checking into the header is definitely very cool, it’s mostly unnecessary since the other flags should let you know if the email is suspicious. When in doubt, ask your IT team!
About the Author – Steve Hopkins is a Support Professional and Team Lead at Rocket IT. Steve and his wife are growing their family through adoption. They have already adopted two sons.
Related Posts
Subscribe to Rocket IT's Newsletter
Stay up to date on trending technology news and important updates.

Find out if Rocket IT is the right partner for your team
Claim a free consultation with a technology expert.