What Happens When You Download an Email Attachment?

When opening an email and clicking the attachment held inside, do you ever think about what goes on behind the scenes; before and after that file is clicked?
For unprotected individuals, the outcome is rather straightforward. You click, cross your fingers, and hope you can trust the source. But let’s say you’re serious about your organization’s cybersecurity, and you’ve invested in modern technology to keep your inbox and team secure. How effective is Rocket IT’s Enhanced Security package in comparison to outdated alternatives?
To get an idea, check out the infographic below. And should you have any questions about email security after taking a look, feel free to contact our team by filling out the form at the bottom of the page or by giving us a call at 770.441.2520.
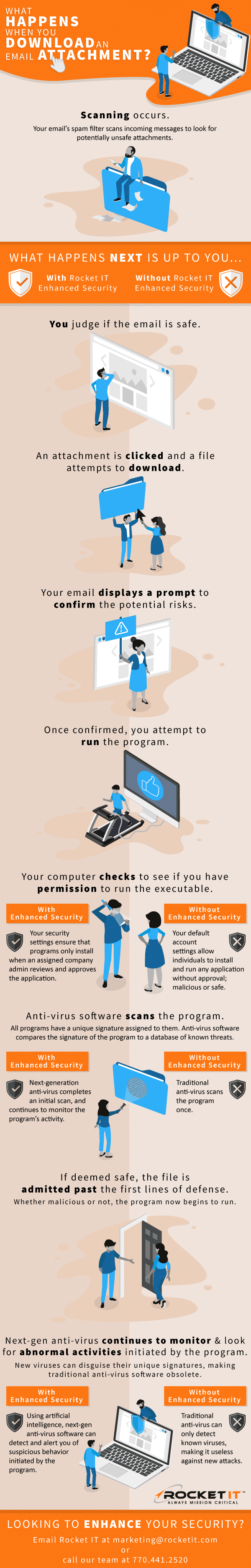
Text Version of Infographic Above:
- Scanning occurs.
- Your email’s spam filter scans the message to look for potentially unsafe attachments.
- You judge if the email is safe.
- An attachment is clicked and a file attempts to download.
- Your email displays a prompt to confirm the potential risks.
- Once confirmed, you attempt to run the program.
- Your computer checks to see if you have permission to run the executable.
- With Rocket IT Enhanced Security: Your security settings ensure that programs only install when an assigned company admin reviews and approves the application
- Without Rocket IT Enhanced Security: Your default account settings allow individuals to install and run any application without approval; malicious or safe.
- Anti-virus software scans the program.
- All programs have a unique signature assigned to them. Anti-virus software compares the signature of the program to a database of known threats.
- With Rocket IT Enhanced Security: Next-generation anti-virus completes an initial scan, and continues to monitor the program’s activity.
- Without Rocket IT Enhanced Security: Traditional anti-virus scans the program once.
- If deemed safe, the file is admitted past the first lines of defense.
- Whether malicious or not, the program now begins to run.
- Next-gen anti-virus continues to monitor & look for abnormal activities initiated by the program.
- New viruses can disguise their unique signatures, making traditional anti-virus software obsolete.
- With Rocket IT Enhanced Security: Using artificial intelligence, next-gen anti-virus software can detect and alert you of suspicious behavior initiated by the program.
- Without Rocket IT Enhanced Security: Traditional anti-virus can only detect known viruses, making it useless against new attacks.
Related Posts
Subscribe to Rocket IT's Newsletter
Stay up to date on trending technology news and important updates.

Find out if Rocket IT is the right partner for your team
Claim a free consultation with a technology expert.










